Why Data Science Isn't an Exact Science
Information Week
JULY 27, 2020
Organizations adopt data science with the goal of getting answers to more types of questions, but those answers are not absolute.

Information Week
JULY 27, 2020
Organizations adopt data science with the goal of getting answers to more types of questions, but those answers are not absolute.

Information Week
JULY 31, 2020
Data science algorithms are never a one-size-fits-all solution. Do you know what makes sense for your business?
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
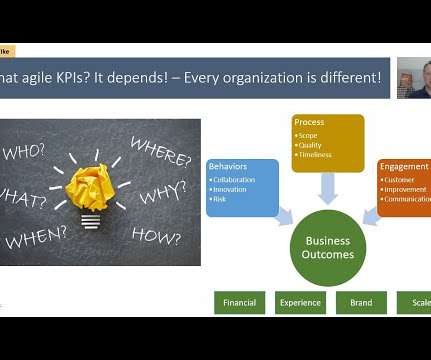
Social, Agile and Transformation
JULY 27, 2020
I'm asked this question on selecting agile KPIs all the time from leaders. . Some want to try measuring agile methodologies with the same project management measurements that worked for them in the past, while others are trying to establish some oversight on a process that they don' fully understand.

Forrester IT
JULY 29, 2020
Forrester’s view on the future of banking is here – examining the changes that we expect to play out over the next decade of retail banking. The drivers of the future are evolutions of the past – some playing out now, others that will be far more prominent by 2025 and table stakes by 2030. […].

Advertiser: ZoomInfo
Sales and marketing leaders have reached a tipping point when it comes to using intent data — and they’re not looking back. More than half of all B2B marketers are already using intent data to increase sales, and Gartner predicts this figure will grow to 70 percent. The reason is clear: intent can provide you with massive amounts of data that reveal sales opportunities earlier than ever before.

CTOvision
JULY 29, 2020
Read Ariadna Miret take a look at what artificial intelligence and machine learning bring to threat intelligence on Security Boulevard : Too much information and not enough time. This, and […].

Association of Information Technology Professional
JULY 27, 2020
If you want to move up at the help desk, a tier II IT support technician may be a good next step for you. Keep reading to learn what a tier II tech does and how to get there.
Information Technology Zone brings together the best content for IT professionals from the widest variety of industry thought leaders.
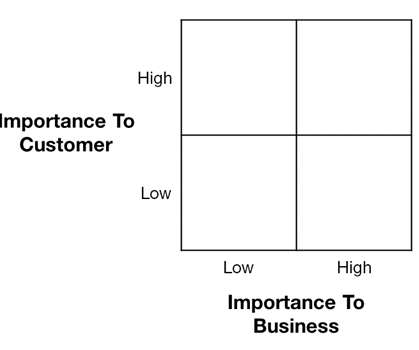
Forrester IT
JULY 28, 2020
Prioritization is the art and science of making decisions, an active process of choosing one thing over another. Just like we all need some form of prioritization in our day-to-day activities, whether we’re thinking about how to tackle our current day’s workload or household chores, companies need prioritization processes and approaches that ensure decisions are […].

CTOvision
JULY 29, 2020
Read Subbarao Kambhapati take a look at why artificial intelligence technology is biased on The Hill: A machine-learned AI system used to assess recidivism risks in Broward County, Fla., often […].

Association of Information Technology Professional
JULY 31, 2020
In July 2020, CompTIA podcasts offered a preview of ChannelCon Online as well as discussions about the future of the tech industry, cybersecurity during the pandemic, the launch of the CompTIA ISAO, and more.

Tech Republic Security
JULY 28, 2020
Read about the saga of Facebook's failures in ensuring privacy for user data, including how it relates to Cambridge Analytica, the GDPR, the Brexit campaign, and the 2016 US presidential election.

Advertiser: GEP
For years, you and your team have fought an uphill battle. Supply disruptions. Cost pressures. ESG compliance. You name it, and you’ve had to navigate it. In 2025, many challenges will persist, but procurement and supply chain teams have a powerful tool with rapidly advancing capabilities to tackle them — artificial intelligence (AI). The GEP Outlook 2025 report examines the disruptive transformation AI is driving in procurement and supply chains, alongside other key trends and the macroeconomic

Forrester IT
JULY 28, 2020
A decade ago I completed the first ever assessment of Australia’s emerging “trusted” or private Infrastructure-as-a-Service (IaaS) market. I followed this up with a 2010 opinion-editorial calling for improved “cloud computing regulation” in Australia as a model for global oversight of a hugely important market segment.

CTOvision
JULY 29, 2020
Read why Pallavi Datta says that insider threat is the biggest contributor to cyberattacks on Security Boulevard : In 2019, a renowned cloud hosting company fell victim to a data […].

Information Week
JULY 29, 2020
Here's how IT leaders can better manage the bias that becomes embedded in algorithms and datasets to help increase opportunities for minority tech professionals.

Tech Republic Security
JULY 29, 2020
While 56% of Americans want more control over personal data, more than 40% said they reuse passwords, use public Wi-Fi, or save a credit card to an online store, KPMG found.

Speaker: Carolyn Clark and Miriam Connaughton
Forget predictions, let’s focus on priorities for the year and explore how to supercharge your employee experience. Join Miriam Connaughton and Carolyn Clark as they discuss key HR trends for 2025—and how to turn them into actionable strategies for your organization. In this dynamic webinar, our esteemed speakers will share expert insights and practical tips to help your employee experience adapt and thrive.

Forrester IT
JULY 31, 2020
Low-code platforms speed delivery of applications, but are they secure? The answer is more complicated than I expected when I started this research project with my colleagues, John Bratincevic and John R. Rymer. We’re still gathering information, but we’ve discovered that: Low-code security is not well understood. Even vendors with extensive security investments acknowledged that […].

CTOvision
JULY 27, 2020
Read Kathleen Walch’s article in Forbes about how AI is making shopping more conversational. A few decades ago, if a person wanted to buy something they had to physically go […].
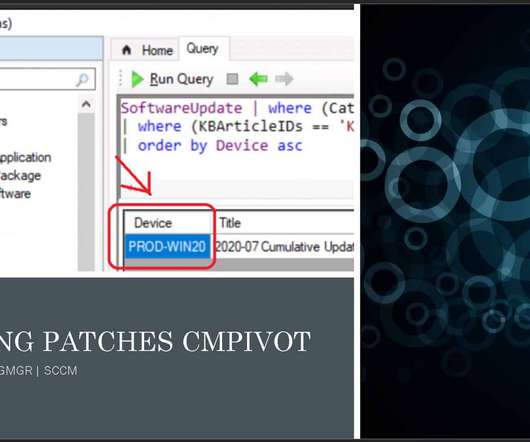
Anoop
JULY 28, 2020
Subscribe YouTube Channel [link]. and Facebook Page to get latest updates. [link]. Let’s Find Missing Patches using ConfigMgr CMPivot Query. I have seen many questions in HTMDForum that we want the patch report using the SQL query. In this post, you will learn how to use the SCCM CMPivot query to find out missing patches. You can customize the CMPivot query as per your need and requirement.

Tech Republic Security
JULY 31, 2020
Experts weigh in to share their thoughts on the hottest topics to expect at this year's all-digital Black Hat conference.

Advertisement
Large enterprises face unique challenges in optimizing their Business Intelligence (BI) output due to the sheer scale and complexity of their operations. Unlike smaller organizations, where basic BI features and simple dashboards might suffice, enterprises must manage vast amounts of data from diverse sources. What are the top modern BI use cases for enterprise businesses to help you get a leg up on the competition?

Forrester IT
JULY 28, 2020
The novel coronavirus shut down the US economy, freezing US consumer spending. This, however, is a temporary situation – consumers will resume spending when it is safe again for them to conduct regular commerce. So, the question customer experience (CX) professionals must ask their businesses is, “Are we positioned to recapture our clients once they […].

CTOvision
JULY 29, 2020
Google LLC said today that its Recommendations AI tool is now publicly available in public beta test mode. Recommendations AI was first announced in private beta in April 2019, and relies […].

Anoop
JULY 31, 2020
Subscribe YouTube Channel [link]. and Facebook Page to get latest updates. [link]. Let’s learn how to troubleshoot out of band hotfix installation logs. You can find more details about the troubleshooting steps in this blog post. SCCM Troubleshooting Out of Band Hotfix Logs | ConfigMgr. NOTE! – More details available Dmpdownloader.log ( DMP Downloader Troubleshooting with State Messages).
Tech Republic Cloud
JULY 31, 2020
Microsoft has provided more information on Dataflex, its new low-code platform for building apps and bots directly within Teams.

Advertiser: ZoomInfo
In this exploration, we're diving into predictions about the future of sales. We're talking about a complete shake-up powered by automation and artificial intelligence (AI). These aren't just fancy tools — they're real game-changers. Automation and AI are here to redefine every interaction, making them smarter, faster, and more meaningful. From personalized customer journeys to streamlined sales processes, the goal is to make every moment count, enhancing both efficiency and connection.

Forrester IT
JULY 30, 2020
Marketers today must understand and use myriad technologies to support omnichannel ad strategies and deliver moments-based marketing. But the landscape of 7,000+ options is overwhelming and rapidly evolving, especially as new privacy regulations and tech giants like Apple and Google limit access to consumer data. We just published some research to help marketers keep up. […].

CTOvision
JULY 29, 2020
Read Greg Jensen explains what autonomous IT is on Dark Reading : Artificial intelligence (AI) is a game changer in fighting cybercrime and defending data, and it can be decisive […].
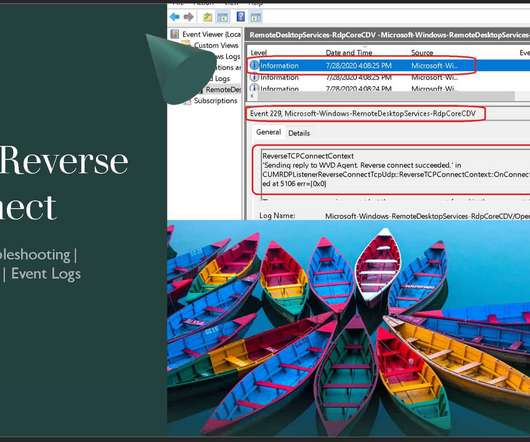
Anoop
JULY 30, 2020
Subscribe YouTube Channel [link]. and Facebook Page to get latest updates. [link]. Let’s quickly go-through the WVD event logs using TCP Reverse Connect technologies. You can check this internal process of RDP connection through the secure channel from Windows 10 devices. I have a WVD Troubleshooting Options Tips Tricks – Windows Virtual Desktop in the previous post.

Tech Republic Security
JULY 28, 2020
The GPS maker scrambled to contain the aftermath of an attack as employees took to social media to describe what was happening.

Advertiser: Procom Services
Procom’s 2024 Salary Guide provides critical insights into the latest hiring trends, in-demand IT roles, and competitive pay rates across Canada and the U.S. It highlights key market dynamics such as the growing demand for remote work, skills-based hiring, and flexible staffing solutions. With detailed pay rate data for top IT positions like Cybersecurity Consultants, Cloud Engineers, and Salesforce Developers, this guide is an essential resource for companies looking to stay competitive in toda

Forrester IT
JULY 27, 2020
Andrew Hewitt, our resident enterprise IT and remote work expert, and I caught up for a quick pulse check on how service providers are faring during the pandemic. Business process outsourcers (BPOs) and contact centers felt the heat from the pandemic a lot more and a lot earlier than other businesses. Even as global brands […].

CTOvision
JULY 29, 2020
Read why Praful Krishna says that information security challenges are proving to be a huge barrier for the artificial intelligence ecosystem on Dark Reading: Information security is all about keeping […].
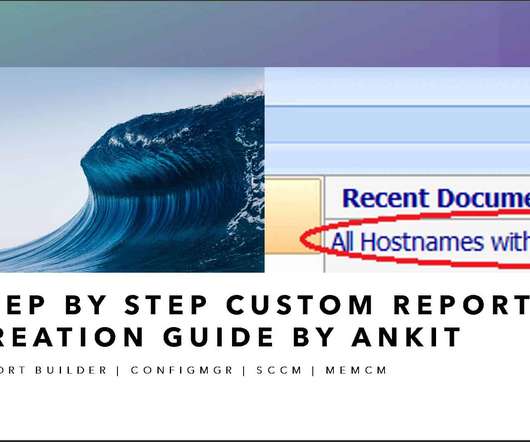
Anoop
JULY 29, 2020
Subscribe YouTube Channel [link]. and Facebook Page to get latest updates. [link]. If you are working as an SCCM Admin in your organization, you might have been asked to create custom reports (Create Custom Report Using Report Builder) according to customer requirements. As an admin, some create WQL queries and some prefer to work on SQL Queries and achieve their desired results.

Information Week
JULY 30, 2020
Looking to get a bigger bang from your budget? Think about optimizing some of your existing IT resources.

Advertisement
For many IT admins, business as usual is a juggling act. Job schedulers and scripts run on autopilot, applications and operating systems can’t speak the same language, and other tools—like RPA or MFT solutions—operate in isolation. On a good day, everything runs smoothly. But good days are rare; more often than not, something goes wrong and you’re stuck putting out fires.
Let's personalize your content