Staff IT Projects to Optimize Team Chemistry
Information Week
FEBRUARY 8, 2023
Behind every successful enterprise IT project is a great project team, but how do you build the right one for your organization?

Information Week
FEBRUARY 8, 2023
Behind every successful enterprise IT project is a great project team, but how do you build the right one for your organization?

Tech Republic Security
FEBRUARY 9, 2023
One of the web's biggest cybersecurity training resources, The Complete 2023 Cyber Security Developer & IT Skills Bundle, is now just $79. The post If your business needs cybersecurity, you should become the expert appeared first on TechRepublic.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

TechSpot
FEBRUARY 6, 2023
Googling programs like MSI Afterburner, Bitwarden, Grammarly, Blender, Gimp, Adobe Reader, Microsoft Teams, OBS, Slack, Thunderbird, and many others lately can bring up promoted search results controlled by hackers. Malvertising campaigns impersonating those brands have subverted Google Ads since at least December.

TechSpot
FEBRUARY 7, 2023
From tech behemoths like Amazon, Google, and Meta, to fintech companies such as Klarna and Stripe, many firms looked at their bottom lines in 2022 and found them wanting. In order to weather a stormy economic outlook, preserve cash, and streamline over-large teams, tech firms scaled back.

Advertiser: ZoomInfo
Sales and marketing leaders have reached a tipping point when it comes to using intent data — and they’re not looking back. More than half of all B2B marketers are already using intent data to increase sales, and Gartner predicts this figure will grow to 70 percent. The reason is clear: intent can provide you with massive amounts of data that reveal sales opportunities earlier than ever before.

Association of Information Technology Professional
FEBRUARY 8, 2023
The principle of least privilege grants users as little access to resources as possible within their role. Learn 3 ways this principle helps secure your environment.

The Accidental Successful CIO
FEBRUARY 8, 2023
There are better ways to find out how your employees are feeling Image Credit: EpicTop10.com In order to be an effective CIO you need to have a good understanding of how your employees are currently feeling. This can be a tricky thing to determine. Traditionally what most CIOs have done is to create a survey and then send it out to have their employees fill it out.
Information Technology Zone brings together the best content for IT professionals from the widest variety of industry thought leaders.

Tech Republic Security
FEBRUARY 7, 2023
With more companies investing in Web 3.0 this year, including blockchain, gaming and the metaverse, the cat and mouse game will continue, but with more dimensions. The post Metaverse adds new dimensions to Web 3.0 cybersecurity appeared first on TechRepublic.

IT Toolbox
FEBRUARY 9, 2023
Find out the tech and career skills needed to succeed in the era of Web3 and blockchain. The post How to Build Tech and Career Skills for Web3 and Blockchain appeared first on Spiceworks.

Forrester IT
FEBRUARY 8, 2023
Consumers shared their attitudes towards subscriptions - see key highlights.

Association of Information Technology Professional
FEBRUARY 10, 2023
Earning CompTIA Security+ helped cybersecurity specialist Vina Ta squash imposter syndrome, deepen her knowledge of IT security and reinforce her passion for working with people.

Advertiser: GEP
For years, you and your team have fought an uphill battle. Supply disruptions. Cost pressures. ESG compliance. You name it, and you’ve had to navigate it. In 2025, many challenges will persist, but procurement and supply chain teams have a powerful tool with rapidly advancing capabilities to tackle them — artificial intelligence (AI). The GEP Outlook 2025 report examines the disruptive transformation AI is driving in procurement and supply chains, alongside other key trends and the macroeconomic

Information Week
FEBRUARY 6, 2023
With individuals set to gain new rights over how businesses use automated decision-making, businesses will have to ensure they're compliant with data privacy and AI regulations.

IT Toolbox
FEBRUARY 10, 2023
Smart inventory management could lead to greater efficacy for industries. Find out other ways AI is enabling transformation. The post How AI Is Transforming Industries With Smart Inventory Management appeared first on Spiceworks.

Forrester IT
FEBRUARY 6, 2023
Digital transformations are notoriously hard. In Forrester's Business And Technology Services Survey, 2022, nearly all services decision-makers have or anticipate challenges in executing their digital transformation. But this does not mean that there is some secret sauce that only a chosen few digital natives possess which remains hidden to the rest of us.

Social, Agile and Transformation
FEBRUARY 6, 2023
I despise the yearly performance management process. Once a year, managers and leaders care enough about their employees’ goals and development plans and must ceremonially record objectives in HR’s performance management system.

Speaker: Carolyn Clark and Miriam Connaughton
Forget predictions, let’s focus on priorities for the year and explore how to supercharge your employee experience. Join Miriam Connaughton and Carolyn Clark as they discuss key HR trends for 2025—and how to turn them into actionable strategies for your organization. In this dynamic webinar, our esteemed speakers will share expert insights and practical tips to help your employee experience adapt and thrive.

Association of Information Technology Professional
FEBRUARY 6, 2023
With technology woven into the fabric of all organizations, an IT curriculum is essential for all academic institutions. Find out why.

IT Toolbox
FEBRUARY 10, 2023
Discover the strategies to achieve profitability amidst economic uncertainty while creating a seamless shopping journey for customers. The post How To Deliver Personalization and Profitability Across Retail Amid Economic Uncertainty appeared first on Spiceworks.

Forrester IT
FEBRUARY 7, 2023
Forrester provides guidance on how to succeed with AI governance with the NIST’s AI RMF 1.0.

Tech Republic Security
FEBRUARY 9, 2023
A new Kaspersky report sheds light on why some tech pros look for jobs on the dark web and how to spot suspicious and likely illegal positions from recruiters in that environment. The post How IT jobs and recruiting on the dark web might trick you appeared first on TechRepublic.

Advertisement
Large enterprises face unique challenges in optimizing their Business Intelligence (BI) output due to the sheer scale and complexity of their operations. Unlike smaller organizations, where basic BI features and simple dashboards might suffice, enterprises must manage vast amounts of data from diverse sources. What are the top modern BI use cases for enterprise businesses to help you get a leg up on the competition?

Information Week
FEBRUARY 10, 2023
Companies feel that they aren't actualizing AI data like they want to. What can they do to better optimize this? Here are some steps that might help juice things up.
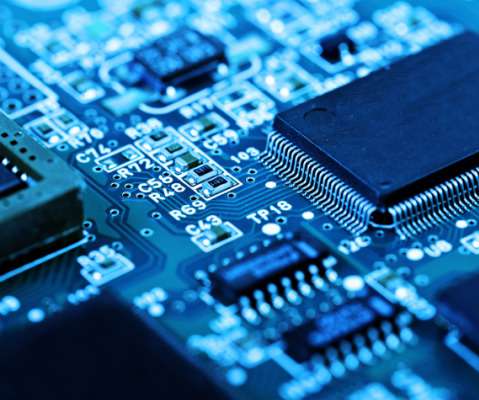
IT Toolbox
FEBRUARY 9, 2023
A motherboard is a circuit board inside computers that stores electrical components and helps them communicate. The post What Is a Motherboard? Definition, Types, Components, and Functions appeared first on Spiceworks.

Forrester IT
FEBRUARY 9, 2023
The world of money is changing, and India has made impressive progress toward innovations in digital payments. India’s central bank, Reserve Bank of India (RBI), is now focusing on Central Bank Digital Currency (CBDC). Things have been a little hazy around the use of cryptocurrencies in India.

Tech Republic Security
FEBRUARY 8, 2023
Ransomware was down last year, though LockBit led threat actors and employees opened a third of the toxic emails in the last six months of 2022. The post New cybersecurity data reveals persistent social engineering vulnerabilities appeared first on TechRepublic.

Advertiser: ZoomInfo
In this exploration, we're diving into predictions about the future of sales. We're talking about a complete shake-up powered by automation and artificial intelligence (AI). These aren't just fancy tools — they're real game-changers. Automation and AI are here to redefine every interaction, making them smarter, faster, and more meaningful. From personalized customer journeys to streamlined sales processes, the goal is to make every moment count, enhancing both efficiency and connection.

Information Week
FEBRUARY 7, 2023
Organizations expect their business and HR leaders to balance functional duties with resource management -- which means stronger investments in AI, advanced analytics, and ML.

IT Toolbox
FEBRUARY 7, 2023
Discover the opportunities and challenges for companies in digital advertising this year and how they are using capabilities like automation. The post Why Instagram and Facebook Are the Most Preferred Channels for Advertising This Year appeared first on Spiceworks.

Forrester IT
FEBRUARY 9, 2023
Our recent 2022 survey found that among the APAC data and analytics decision-makers, only 13% indicated that their enterprise has advanced insights-driven business maturity — that is, they use a decide-act-learn-improve loop to ensure that insights are having maximum business impact.

Association of Information Technology Professional
FEBRUARY 9, 2023
Chris Ward felt like he was repeating the same mistakes. Being able to talk through those challenges with CompTIA peers was a huge step forward for his business.

Advertiser: Procom Services
Procom’s 2024 Salary Guide provides critical insights into the latest hiring trends, in-demand IT roles, and competitive pay rates across Canada and the U.S. It highlights key market dynamics such as the growing demand for remote work, skills-based hiring, and flexible staffing solutions. With detailed pay rate data for top IT positions like Cybersecurity Consultants, Cloud Engineers, and Salesforce Developers, this guide is an essential resource for companies looking to stay competitive in toda

Information Week
FEBRUARY 6, 2023
Data analytics is a powerful, yet limited tool. Don't allow misleading analytics to lead you into faulty decisions.

IT Toolbox
FEBRUARY 6, 2023
Spiceworks speaks with experts on how companies can reduce hiring costs in the technology sector. The post Hiring in Tech: From Employer’s Market to the Candidate’s Market appeared first on Spiceworks.

Forrester IT
FEBRUARY 9, 2023
It’s no secret that in today’s business climate, corporate banks are feeling the squeeze. They struggle with an installed base of pre-modern applications and archaic processes. Now is the time when corporate banks change the way they serve clients.

Association of Information Technology Professional
FEBRUARY 7, 2023
The metaverse is not a new idea, but the people engaging with it are bringing new ideas and use cases every day.

Advertisement
For many IT admins, business as usual is a juggling act. Job schedulers and scripts run on autopilot, applications and operating systems can’t speak the same language, and other tools—like RPA or MFT solutions—operate in isolation. On a good day, everything runs smoothly. But good days are rare; more often than not, something goes wrong and you’re stuck putting out fires.
Let's personalize your content