Email malware targets U.S. senator and military
Tech Republic Security
JANUARY 22, 2020
The cybercriminals behind the powerful banking malware have turned their attention to government targets like Sen. Cory Booker.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Tech Republic Security
JANUARY 22, 2020
The cybercriminals behind the powerful banking malware have turned their attention to government targets like Sen. Cory Booker.

Tech Republic Security
SEPTEMBER 27, 2021
Commercially-available malware, with minimal modification, is behind attacks against the Indian government, says Cisco's Talos security research group.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

CIO Business Intelligence
MARCH 4, 2025
The report also highlighted that Chinese groups continue to share malware tools a long-standing hallmark of Chinese cyber espionage with the KEYPLUG backdoor serving as a prime example. Vault Panda has used many malware families shared by Chinese threat actors, including KEYPLUG, Winnti, Melofee, HelloBot, and ShadowPad.

Tech Republic Security
MARCH 21, 2022
The malware has been found in the French construction and government sectors and uses steganography, Tor proxy and package installer software, Proofpoint says. The post New Serpent backdoor malware targets French entities with unforeseen method appeared first on TechRepublic.

Tech Republic Security
MARCH 2, 2022
Symantec said that the newly-discovered Daxin exhibits a previously unseen level of complexity, and it’s been targeting governments around the world for some time. The post Daxin: A Chinese-linked malware that is dangerous and nearly impossible to detect appeared first on TechRepublic.

CIO Business Intelligence
MARCH 4, 2025
The report also highlighted that Chinese groups continue to share malware tools a long-standing hallmark of Chinese cyber espionage with the KEYPLUG backdoor serving as a prime example. Vault Panda has used many malware families shared by Chinese threat actors, including KEYPLUG, Winnti, Melofee, HelloBot, and ShadowPad.

Network World
OCTOBER 11, 2024
It cited the MGM Resorts data breach, the Microsoft email hack, and the FBot malware targeting web servers, cloud services, and software-as-a-service, which achieves persistency and propagates on AWS via AWS IAM (identity and access management) users as three examples of how the keys could be abused.
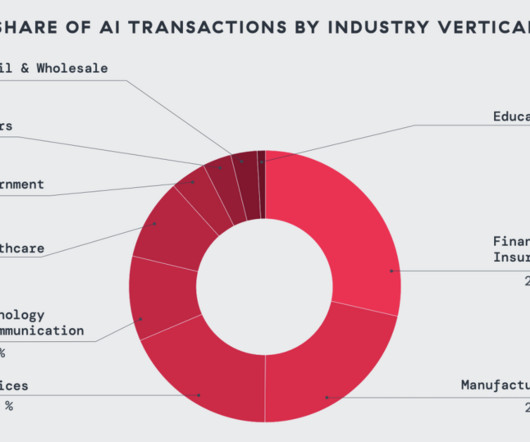
CIO Business Intelligence
MARCH 25, 2025
As organizations work to establish AI governance frameworks, many are taking a cautious approach, restricting access to certain AI applications as they refine policies around data protection. AI-powered cyberthreat protection: Detect and block AI-generated phishing campaigns, adversarial exploits, and AI-driven malware in real time.

Network World
APRIL 28, 2017
A new malware program that targets macOS users is capable of spying on encrypted browser traffic to steal sensitive information. One of the rogue emails was crafted to look as if it was sent by a Swiss government agency warning recipients about apparent errors in their tax returns.

Network World
MARCH 5, 2019
government. And as a decade-old malware resurfaces in enterprise networks, a report questions if the world is ready for the next large-scale ransomware attack. The ongoing battle between the U.S. and Huawei could soon go to court as Huawei reportedly prepares to sue the U.S.

Network World
DECEMBER 1, 2016
Saudi Arabia's government agencies were hit with a cyberattack that security researchers are blaming on a worm-like malware that can wipe computer systems, destroying data. Several government bodies and vital installations suffered the attack, disrupting their servers, the country's Saudi Press Agency said on Thursday.

Network World
MAY 5, 2017
Over the past year, a group of attackers has managed to infect hundreds of computers belonging to government agencies with a malware framework stitched together from JavaScript code and publicly available tools.

Network World
AUGUST 29, 2016
Security researchers have found a sophisticated malware program that may have been used recently by a gang of hackers to steal more than US$350,000 from ATMs in Thailand. million Baht from 21 ATMs in the country. million Baht from 21 ATMs in the country. To read this article in full or to leave a comment, please click here

Network World
OCTOBER 21, 2024
In response, businesses and governments began to invest more heavily in cybersecurity measures, such as intrusion detection systems, encryption, and security awareness training. As we entered the 2000s, cyberattacks became more sophisticated and targeted.

CIO Business Intelligence
NOVEMBER 29, 2022
trillion by 2025 — more than double what was spent in 202 As organizations amp up their digital transformation initiatives, which are critical for survival in today’s business climate, they must also consider how to modernize and migrate sensitive data and how it is managed and governed. Data Management

Network World
AUGUST 27, 2024
Target customers are enterprises and telecom service providers looking to defend against malware and ransomware attacks, and to defend against nation-state actors. VMware’s vDefend platform protects east-west traffic with zero trust, microsegmentation, zone-level segmentation, and malware and ransomware defense.

Network World
SEPTEMBER 7, 2017
The ever-widening scope and unbelievable variety of threats makes keeping these devices safe from cyber criminals and malware a full-time challenge for companies, governments and individuals around the world. Ensuring cybersecurity for computers and mobile phones is a huge, complex business.

CTOvision
DECEMBER 12, 2018
A cyber espionage group is deploying a new type of trojan malware against telecommunications, information technology, and government organisations.

CTOvision
DECEMBER 19, 2014
It is true they have been wrong before, and it is a very American trait to be skeptical of government assessments. government departments and agencies, the FBI now has enough information to conclude that the North Korean government is responsible for these actions. government has previously linked directly to North Korea.

CIO Business Intelligence
MARCH 24, 2025
Some of the leading cybersecurity certifications being pursued in the healthcare sector include: CISSP (Certified Information Systems Security Professional) a globally respected credential covering security architecture, risk management, and governance.

Network World
AUGUST 1, 2016
Russian military networks and other critical infrastructure have been hit by tailor-made malware, according to government officials. Analysis of the attack showed that filenames, parameters and infection methods used in the malware are similar to those involved in other high-profile cyber-espionage operations around the world.

CIO Business Intelligence
MARCH 19, 2025
Attackers now have access to extensive identity data from multiple sourcesincluding data breaches, infostealer malware infections, phishing campaigns, and combolistsposing a challenge for organizations whose security measures have not yet adapted to address the full scope of interconnected identity exposures holistically.

Forrester IT
MAY 15, 2017
Unless you have been living under a rock or possibly hiding in the mountains of Montana with a giant beard and eating way too many government issued MRE's you probably heard about the nuclear bomb of a ransomware attack that kicked off last week. Data is the perimeter, defend it that way. Welcome to the post apocalypse folks. Cyber Attacks.

CTOvision
APRIL 7, 2014
in new contracts for advanced cybersecurity projects for defense and federal government agencies in the areas of cloud-based advanced malware analysis, spear-phishing attacks against Android, and big data analytics for compromise detection. FAIRFAX, VA—April 7, 2014 —Invincea, Inc., contract with the U.S. Videos: [link].

Network World
MAY 9, 2017
In late March when I got an unsettling message on my Gmail account: "Warning: Google may have detected government-backed attackers trying to steal your password." Google sends them out when it detects a "government-backed attacker" has attempted to hack an account through phishing or malware.

Network World
JANUARY 24, 2017
The disk-wiping Shamoon malware, which was used in attacks that destroyed data on 35,000 computers at Saudi Aramco in 2012, is back; the Shamoon variant prompted Saudi Arabia to issue a warning on Monday. An alert from the telecoms authority, seen by Reuters, warned all organizations to be on the lookout for the variant Shamoon 2.

CTOvision
DECEMBER 19, 2013
By Bob Gourley SecureNinjaTV’s Alicia Webb continues our coverage of FEDcyber 2013 by speaking with Guidance Software’s Bob Greenberg about insider threat, vulnerabilities and malware attacks. The 3rd annual Government-Industry event drew over 300 industry professionals for a busy day of action-oriented discussions.

Network World
MAY 4, 2017
It targets government entities, intelligence agencies, embassies, military organizations, research and academic institutions and large corporations. The group, known in the security industry as Snake, Turla or Uroburos, has been active since at least 2007 and has been responsible for some of the most complex cyberespionage attacks.

Dataconomy
FEBRUARY 13, 2025
The Silicon Valley security provider AppSOC discovered significant vulnerabilities, including the ability to jailbreak the AI and generate malware. You could in some cases, generate actual malware which is a big red flag,” he stated. “It failed a bunch of benchmarks where you could jailbreak it.

Tech Republic Security
JUNE 27, 2017
Bill Detwiler talks to TechRepublic's Dan Patterson about the big takeaways from the Global Cybersecurity Summit 2017 in Kiev, Ukraine and the growing security threats from IoT devices and machine-learning-created malware.

Tech Republic Security
JANUARY 23, 2023
A new report from Kaspersky details what their digital forensics and incident response teams predict as the main 2023 threats to corporations and government agencies. Learn more about it. The post Kaspersky releases 2023 predictions appeared first on TechRepublic.

Galido
MARCH 2, 2020
Information Technology Blog - - List of Latest Malware Attacks in the World - Information Technology Blog. Malware in different forms has caused serious data loss to users around the world in the last few decades. Here, we have listed the latest malware attacks in the world that you should be aware of. Ryuk Ransomware.

CIO Business Intelligence
MARCH 31, 2025
If agents are compromised, attackers can use them to move laterally across the network, escalate their privileges to steal data, deploy malware and hijack critical internal systems. Unfortunately, many of the permissions given to AI agents are far too broad. Machines, on the other hand, dont complain.

Network World
MAY 14, 2017
National Security Agency has affected customers around the world, and described the spread of the WannaCrypt ransomware on Friday in many countries as yet another example of the problems caused by the stockpiling of vulnerabilities by governments.

Gizmodo
JANUARY 19, 2021
On Monday, researchers announced the discovery of yet another malware strain used by foreign hackers to infiltrate a wide milieu of American government agencies and companies. SolarWinds: it’s the hack that keeps on growing. Read more.

Network World
JUNE 27, 2017
In as little as four hours, the bad guys can reverse engineer a software patch for an open-source content management system (CMS) and build an exploit capable of turning millions of websites into spammers, malware hosts or DDoS attackers. To read this article in full or to leave a comment, please click here

CTOvision
DECEMBER 16, 2013
“In June of 2013, we began shipping a solution powered by Invincea — Dell Data Protection | Protected Workspace — to provide our customers with advanced malware protection out of the box. Invincea is the premier innovator in advanced malware threat detection, breach prevention, and forensic threat intelligence.

CTOvision
APRIL 3, 2019
Read why Steve Ranger says that phishing attacks are more disruptive than ransomware, malware or hacking on ZDNet : Phishing and fake emails are the biggest security headache for business and among the hardest to tackle.

CTOvision
AUGUST 11, 2014
The legislation encourages threat information sharing between government and the private sector. CISA considerations for commercial and government entities. Big Data CTO Cyber Security DoD and IC Bob Gourley Chris Petersen CISA Cognitio Corp Computer security Cybersecurity Malware' Bob Gourley, Partner of Cognitio Corp.

CTOvision
DECEMBER 19, 2013
By Bob Gourley SecureNinjaTV’s Alicia Webb continues our coverage of FEDcyber 2013 by speaking with Triumfant’s President & CEO John Prisco about malware detection and remediation. The 3rd annual Government-Industry event drew over 300 industry professionals for a busy day of action-oriented discussions.

Network World
SEPTEMBER 12, 2024
AI is really a toolkit made up largely of machine learning and LLMs, many of which have been applied for over a decade to tractable problems like novel malware detection and fraud detection. In the short term, the adversaries in particular are going to get better at phishing and malware generation. But there’s more to it than that.

SecureWorld News
NOVEMBER 2, 2022
New research from Lookout reveals the most common mobile threats aimed at federal, state, and local government agencies and their employees—all of which have increased since 2021. One in eight government employees were exposed to phishing threats. Federal workers have more restrictions on BYOD devices.

CTOvision
SEPTEMBER 5, 2013
White House looks to public for ideas on open gov – “The first National Action Plan on Open Government was released in September 2011 and laid out 26 steps to promote increased transparency, public participation in government and more efficient management of public resources.” ” Via FedScoop, more here.

The Verge
JULY 12, 2021
Microsoft says it’s gone door-to-door replacing routers compromised with the Trickbot malware in Brazil and Latin America, hoping to squash an international hacking group. Eradicating malware from routers can be particularly difficult for users , making in-person replacement a surprisingly effective tactic.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content