Data Governance for 2020 and Beyond
Forrester IT
JUNE 10, 2020
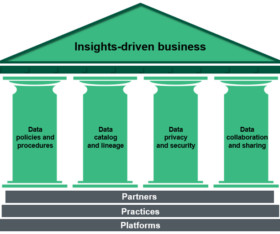
Companies have short attention spans when it comes to data governance. To address these expansions, data owners either search for the simple approach or re-educate on data governance 101. Here is the […].



















































Let's personalize your content