Considering a Career as an IT Hardware Engineer?
Information Week
NOVEMBER 8, 2023
Often toiling in the shadow of their software counterparts, hardware engineers play a critical role in advancing IT. Learn why and how to join the team.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Information Week
NOVEMBER 8, 2023
Often toiling in the shadow of their software counterparts, hardware engineers play a critical role in advancing IT. Learn why and how to join the team.

CIO Business Intelligence
DECEMBER 2, 2024
This balances debt reduction and prioritizes future strategic innovations, which means committing to continuous updates, upgrades, and management of end-user software, hardware, and associated services. Our research reveals that top performers allocate around 15% of their IT budget to debt remediation.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

CIO Business Intelligence
NOVEMBER 1, 2024
1] HP Managed Collaboration Services includes hardware, repair services, and analytics components and may include financing. To register for access, visit [link] Some features and capabilities may require additional purchase of HP services and/or commercial hardware capable of supporting the HP Insights agent for Windows, Mac, & Android.
Tech Republic Security
APRIL 5, 2022
Customers of hardware wallet provider Trezor have been targeted by a phishing scam, resulting in the theft of cryptocurrency assets. See how it works and how to protect yourself from this new threat. The post Sophisticated phishing attacks steal Trezor’s hardware wallets appeared first on TechRepublic.

CIO Business Intelligence
NOVEMBER 19, 2024
Intel’s cloud-optimized hardware accelerates AI workloads, while SAS provides scalable, AI-driven solutions. Their collaboration enables real-time delivery of insights for risk management, fraud detection, and customer personalization.

Tech Republic Security
SEPTEMBER 4, 2020
If you migrated to a different iPhone or Android device and need to transfer Google Authenticator to the new hardware, follow these steps.

Network World
MAY 28, 2024
Keep in mind, this is an optional feature for network devices and support for it isn’t required for hardware to be Wi-Fi 6 or WPA3-compliant. While many newer network devices are WPA3-compatible, older hardware may require updates or replacements. Also remember there’s no authentication with OWE, meaning any client can connect.

CIO Business Intelligence
FEBRUARY 18, 2025
These savings were found through decommissioning legacy data centers, physical equipment, and hardware, including sunsetting legacy DLP tools, SWG technology, firewalls, and related hardware and circuitry. That amounted to 10% infrastructure cost savings.
Network World
DECEMBER 20, 2024
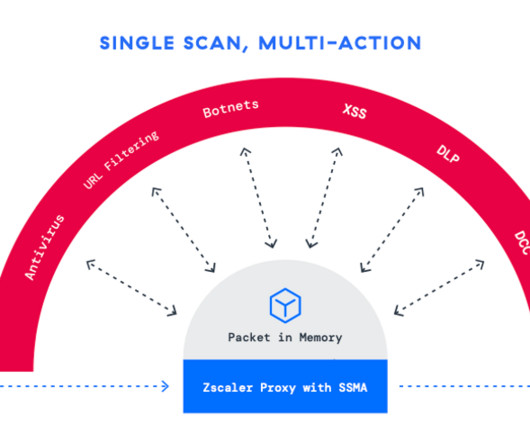
Unlike traditional hardware-based solutions that force organizations to compromise between security and speed, Zscalers cloud-native approach allows organizations to fully inspect traffic at scale with its Single Scan, Multi-Action enginea unique feature that processes traffic once to apply multiple security controls simultaneously.

IT Toolbox
AUGUST 8, 2023
Data storage evolution: from hardware limits to cloud-driven opportunities. Learn how to stay ahead in the growing datasphere. The post Unleashing Data Storage: From Hardware to the Cloud appeared first on Spiceworks.

Tech Republic Security
NOVEMBER 17, 2020
If you migrated to a different iPhone or Android device and need to transfer Google Authenticator to the new hardware, follow these steps.

Anoop
JANUARY 1, 2021
Let’s check ConfigMgr Hardware Related Reports available in the latest version. Some of the reports from the hardware category of reports are not relevant to me. The post ConfigMgr Hardware Related Reports | SCCM | Default appeared first on How to Manage Devices by Anoop C Nair. Subscribe YouTube Channel [link].

CIO Business Intelligence
OCTOBER 25, 2024
If there’s any doubt that mainframes will have a place in the AI future, many organizations running the hardware are already planning for it. Many Kyndryl customers seem to be thinking about how to merge the mission-critical data on their mainframes with AI tools, she says.

Anoop
FEBRUARY 9, 2021
Let’s understand the ConfigMgr Client Action called Hardware Inventory Collection Cycle in a bit more. Read More ConfigMgr Client Action Hardware Inventory Collection Cycle | SCCM. The post ConfigMgr Client Action Hardware Inventory Collection Cycle | SCCM appeared first on How to Manage Devices by Anoop C Nair.

SecureWorld News
DECEMBER 8, 2024
Ensure quantum-ready hardware: Require that new infrastructure device purchases, such as routers and firewalls, have quantum-resistant or upgradable firmware. Static firmware means that hardware must be replaced every time there is a security issue, which can be costly and inefficient.
Anoop
JANUARY 4, 2021
The ConfigMgr Asset intelligence (AI) adds hardware inventory classes to collect more detailed information from Configuration Manager clients. This data includes the hardware and software titles used in your workplace environment. Subscribe YouTube Channel [link]. and Facebook Page to get latest updates.

CTOvision
JULY 21, 2020
Bradley Geden, director of product marketing at Synopsys, looks at how to take advantage of repeatability, […]. As AI chips become more pervasive, three primary approaches are moving to the forefront.
Tech Republic Security
SEPTEMBER 25, 2023
In this step-by-step tutorial, Jack Wallen explains how to easily create and copy SSH keys. SSH keys provide a secure and convenient way to authenticate remote servers.

CIO Business Intelligence
FEBRUARY 1, 2024
And there could be ancillary costs, such as the need for additional server hardware or data storage capacity. Here are some costs that will need to be included in your analysis: Hardware: Do I need to buy new hardware, or do I have capacity to run the software on existing servers and storage?

Network World
FEBRUARY 3, 2025
A challenge for enterprises that operate large-scale network infrastructure has long been how to maintain performance while updating critical systems. The Linux Foundations networking division (LF Networking) is helping to address that challenge with the L3AF project, which is based on eBPF (extended Berkeley Packet Filter ) technology.

Network World
DECEMBER 16, 2024
Despite the fact that we seem to be years away from having practical working quantum computers, or even a common set of standards for how to build these things, investors, governments, and large corporations are taking quantum computing seriously. Quantinuum provided the quantum hardware and Microsoft handled the error correction.
Anoop
DECEMBER 28, 2020
Let’s check how to Launch ConfigMgr Reports. How many of you use these SCCM default reports related to Hardware or Asset Intelligence or Software Updates? The post How to Launch ConfigMgr Reports | SCCM | Default Reports appeared first on How to Manage Devices by Anoop C Nair.

Network World
NOVEMBER 22, 2024
Optimize IT service management (ITSM) by handling basic troubleshooting (level 1 and level 2 support) such as password resets or simple hardware glitches. How to get started with an AI networking strategy AI networking solutions are offered through a variety of different formats.

CIO Business Intelligence
JANUARY 20, 2023
Some are relying on outmoded legacy hardware systems. Most have been so drawn to the excitement of AI software tools that they missed out on selecting the right hardware. Dealing with data is where core technologies and hardware prove essential. Those that do so will find their data and applications to be force multipliers.

CIO Business Intelligence
AUGUST 8, 2024
In addition to swapping out expensive commercial models for open source ones, or small language models (SLMs), KPMG is also experimenting with alternatives to traditional AI processing hardware. And people were getting subscriptions to gen AI products they didn’t know how to use.

CIO Business Intelligence
JUNE 21, 2022
Let’s cut to the chase: As a CEO or CIO dealing with a continual barrage of unexpected business and societal disruptions, you probably focus on two things: How to innovate faster when the next “new normal” smacks you in the face, and how to create an organization that’s better at adapting over the longer term.

CIO Business Intelligence
JANUARY 6, 2023
These IT pros typically have a bachelor’s degree in computer science and should be knowledgeable in LAN/WAN protocol, software, and hardware. This position involves a lot of time spent troubleshooting, and network and computer systems administrators typically need to be on call in case of an emergency or failure.

Network World
APRIL 4, 2025
We will spin it off, but really focus on our core business and how to expand that using AI and software. He said that in the past, Intel designed hardware, then partners had to figure out developing the software to make it work. The world has changed. You have to flip that around.

Network World
JULY 22, 2024
With data collected from a wider ranges of sources, network observability tools promise to provide actionable guidance on how to resolve performance problems before they impact end users and customers.

Information Week
JUNE 8, 2023
Feeling overwhelmed by expensive hardware and software support contracts? There is an alternative option thanks to advancements in IT orchestration and automation.

Network World
JANUARY 31, 2025
Or is NaaS something fundamentally different that addresses a growing challenge for network execs: how to provide network connectivity, resiliency, security, and scalability in a multicloud world? Managed service: Subscription-based hardware plus a managed service to operate it.

Network World
APRIL 28, 2021
This article tells where it came from and how it works. is a standard that defines how to provide authentication for devices that connect with other devices on local area networks (LANs). How to deploy 802.1x IEEE 802.1X for Wi-Fi using WPA3 enterprise. To read this article in full, please click here

CIO Business Intelligence
NOVEMBER 15, 2024
Mayorkas, which, the release said, “determined the need for clear guidance on how each layer of the AI supply chain can do their part to ensure that AI is deployed safely and securely in US critical infrastructure.”

CIO Business Intelligence
JUNE 18, 2024
As the race to deploy artificial intelligence (AI) hits a fever pitch across enterprises, the savviest organizations are already looking at how to achieve artificial consciousness—a pinnacle of technological and theoretical exploration. The hardware requirements include massive amounts of compute, control, and storage.

Network World
APRIL 4, 2022
How to choose an edge gateway. FortiOS is the vendor’s operating system for the FortiGate family of hardware and virtual components. FortiOS 7.2, has 300 new features including AI support to help stop network threats more quickly, sandboxing to help fight ransomware threats, and improved SD-WAN , branch, and edge orchestration.

CIO Business Intelligence
SEPTEMBER 12, 2022
IT hardware: desktops, microcomputers, peripherals, printers, scanners. The government makes a distinction between hardware and software and services, each of which have their own Source List or Standing Offers contracts. IT software service connectivity, productivity, and security software Enterprise-wide solutions.

Network World
AUGUST 29, 2024
In the analyst call , Huang also explored his view of the future of enterprise computing, and the massive degree to which AI is going to change the nature of hardware and computing operations. “We The CEO also argued that the financial underpinnings of IT environments are also changing rapidly.

Tech Republic Cloud
JULY 19, 2021
Jack Wallen introduces you to the ChromeOS Diagnostic tool, with which you can run hardware tests on your Chromebook. Is your Chromebook acting up?

CIO Business Intelligence
APRIL 18, 2023
With no pressure to recommend a specific system, vendor, hardware or software product, independent fractional CIOs can thoroughly analyze various options, test those options, and make decisions that best serve the organization,” Hartman says.

CIO Business Intelligence
MAY 28, 2022
By 2025, IDC research shows, 90% of the Global 2000 will bring their sustainability mandates to the IT agenda, insisting on use of reusable materials in hardware supply chains, carbon neutrality targets for IT facilities, and lower energy use as prerequisites for doing business.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content