Red Hat to acquire Neural Magic
Network World
NOVEMBER 12, 2024
Red Hat intends to democratize the power of AI through open-source-licensed models that can run anywhere.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Network World
NOVEMBER 12, 2024
Red Hat intends to democratize the power of AI through open-source-licensed models that can run anywhere.

Network World
MARCH 17, 2025
Broadcoms decisions to replace perpetual VMware software licenses with subscriptions and to eliminate point products in favor of an expensive bundle of private cloud tools are driving longtime VMware customers to look for an exit strategy. For customers looking elsewhere, theres no shortage of alternatives. McDowell agrees.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Network World
MARCH 10, 2025
The Court found that these parties had conspired to breach Winsopias license agreement in a deliberate, systematic and intentionally hidden effort to unlawfully reverse engineer critical IBM mainframe technology. IBM licensed its mainframe software to Winsopia beginning in 2013, according to the court documents.

CIO Business Intelligence
JULY 5, 2024
The landscape of data center infrastructure is shifting dramatically, influenced by recent licensing changes from Broadcom that are driving up costs and prompting enterprises to reevaluate their virtualization strategies. As a result, VMware customers can no longer purchase perpetual licenses or just the ESXi hypervisor on its own.

Network World
MARCH 13, 2025
Whats inside VergeIO and where its deployed While the ESX hypervisor is at the core of the VMware virtualization platform, VergeIO is based on the open-source KVM hypervisor. The software requires direct hardware access due to its low-level integration with physical resources.

CIO Business Intelligence
JULY 3, 2024
A VMware licensing cost increase of 150%. For many VMware customers, the licensing model and price changes were abrupt. Facing backlash from existing customers, Broadcom has attempted to explain the new product and licensing model with a hope that current customers can manage the transition. An increase of 300%.
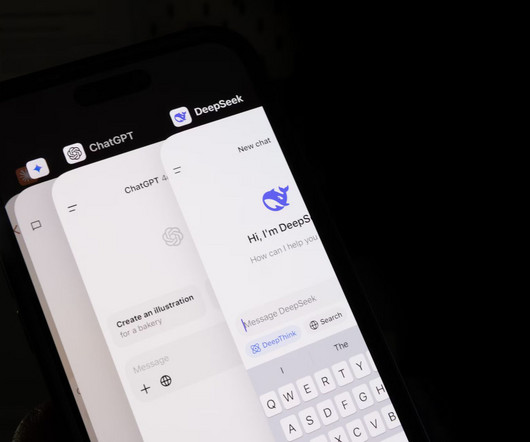
Dataconomy
MARCH 26, 2025
Just a massive set of model weights, an MIT license, and a few technical whispers that were enough to set the AI community ablaze. DeepSeek, however, opted for its trademark under-the-radar approach, quietly uploading 641 GB of data under an MIT license. While some innovations arrive with fanfare, this release was different.

CIO Business Intelligence
DECEMBER 3, 2024
Gone are the days when companies used a single database and had a straightforward cost structure, including hardware and software costs and number of users. Expansion of license types. These different databases have varying licensing mechanisms, including traditional, cloud, full open source, and commercial open source.

CIO Business Intelligence
JULY 18, 2024
By understanding their options and leveraging GPU-as-a-service, CIOs can optimize genAI hardware costs and maintain processing power for innovation.” Open source is one way CIOs can definitely keep the costs low,” he says, pointing out that open-source models are also transparent and can be customized.

Data Center Knowledge
JUNE 21, 2017
Its licensing framework is one of the key differences between LinkedIn’s data center tech foundation and OCP. Read More.

SPF13
MARCH 20, 2015
In the last few years open source has transformed the software industry. From Android to Wikipedia, open source is everywhere, but how does one succeed in it? What Every Successful Open Source Project Needs. Open Source Companies • Redhat $13B • Cloudera $3B • MongoDB $1.6B • Docker $.5B

CIO Business Intelligence
AUGUST 30, 2024
History suggests hyperscalers, which give away basic LLMs while licensing subscriptions for more powerful models with enterprise-grade features, will find more ways to pass along the immense costs of their buildouts to businesses. Can you blame them? Maybe you want to create avatar-based videos that communicate in multiple languages?

CIO Business Intelligence
JULY 5, 2022
There are clear caveats in the HCI world: limitless control is all well and good, but infrastructure details like lack of local storage and slow networking hardware restricting I/O would always define the hard limits on what is possible. Worries around vendor lock-in surround the black-box nature of HCI-in-a-box appliances, too.

CIO Business Intelligence
APRIL 22, 2022
Data science could help an organization build tools to predict hardware failures, enabling the organization to perform maintenance and prevent unplanned downtime. Data science teams make use of a wide range of tools, including SQL, Python, R, Java, and a cornucopia of open source projects such as Hive, oozie, and TensorFlow.

CIO Business Intelligence
AUGUST 16, 2023
Companies are looking at Google’s Bard, Anthropic’s Claude, Databricks’ Dolly, Amazon’s Titan, or IBM’s WatsonX, but also open source AI models like Llama 2 from Meta. Open source models are also getting easier to deploy. We feel that every hyperscaler will have open source generative AI models quickly.”

Dataconomy
FEBRUARY 27, 2025
has expanded its Phi line of open-source language models with the introduction of two new algorithms designed for multimodal processing and hardware efficiency: Phi-4-mini and Phi-4-multimodal. Microsoft Corp. Phi-4-mini and Phi-4-multimodal features Phi-4-mini is a text-only model that incorporates 3.8

CIO Business Intelligence
JUNE 15, 2022
Maintained audit control of open source applications running in your cloud-native or containerized workloads? For compliance, all the new licenses need to be audited and kept in a tight review cycle. Open source applications running in the cloud need to be copyrighted.

Network World
SEPTEMBER 4, 2024
The AI model providers (with one exception noted below) are also eager to promote licensing of their generative AI tools. You can’t buy hardware in anticipation of your application needs,” one CIO said. All either group needs is buyers to line up, but the confusion I just mentioned means most don’t even know how to start.

CIO Business Intelligence
NOVEMBER 15, 2023
Confusingly, Microsoft already offers a Sales Copilot; Copilot for Sales is a different product that includes a license for Copilot for Microsoft 365, and helps sales staff prepare for customer meetings by creating custom briefing documents. Here’s some of the top AI news CIOs will want to take away from Microsoft Ignite 2023.

Data Center Knowledge
JULY 15, 2013
Even Facebook, which has open sourced much of its designs for its data center hardware but remains vague about its server count, saying only that it operates “hundreds of thousands” of machines. wow microsoft should be paying more than $1 billion for licensing then. Ruchira Sahan. Posted July 23rd, 2013.
The Verge
JANUARY 8, 2022
Now, Google has launched an open-source API standard called Ripple that could theoretically bring the tech to additional devices outside Google — perhaps even a car, as Ford is one of the participants in the new standard. One commit points out that the project was updated “to include CTA.”)

The Verge
JULY 7, 2020
But Fraunhofer says VVC could be a path forward for the industry, as almost every major hardware and software company is currently tied up in a messy patent royalty system that dictates how much various stakeholders must pay to use different compression and transmission standards for devices, websites, and apps.

Dataconomy
JANUARY 27, 2025
DeepSeek has unveiled yet another major contribution to the open-source AI landscape. Image: DeepSeek Analysts point to DeepSeeks consistent philosophy: keep it open-source, stay privacy-first, and undercut subscription-based rivals.

GeekWire
SEPTEMBER 25, 2024
More recently, regulators have been scrutinizing deals between tech giants and smaller startups that are structured as “ reverse acquihires ,” which include hiring company founders and licensing technology. Its original pitch was to help companies deploy machine learning models on various hardware configurations.

GeekWire
MAY 11, 2023
Engineers may be tempted to use AI-generated computer code to boost productivity, but this can pose ethical and legal risks when it’s too similar to existing open-source code, Moses said. Startups must factor in hardware costs for running large AI models, according to Batalov. How can startups compete with tech giants?

Data Center Knowledge
JULY 25, 2013
Cloudera announced Sentry – a new Apache licensed open source project that delivers the industry’s first fine-grained authorization framework for Hadoop. Amazon has cut prices for dedicated EC2 instances – an instance on single-tenant hardware that is particularly attractive to enterprise customers.

Dataconomy
MARCH 20, 2025
Developed by Google, this open-source framework allows developers and researchers to efficiently model complex data structures and perform high-level computations. TensorFlow is an open-source framework designed for machine learning and deep learning applications. Released as open-source in 2015 under the Apache 2.0

The Verge
MARCH 1, 2022
Hacking group Lapsus$ has claimed responsibility for the attack, and has demanded that Nvidia make its drivers open-source if it doesn’t want more data leaked. We request that NVIDIA commits to COMPLETELY OPEN-SOURCE (and distribute under a foss license) their GPU drivers”. “We

Dataconomy
MARCH 12, 2025
Despite initial uncertainty regarding interest in such models, the popularity of alternatives like DeepSeek indicates demand for AI technologies with lower hardware requirements. What “open” or “open source” means within the context of AI models remains debated. technology.

Chief Seattle Greek Blog
MARCH 2, 2009
In this environment, it sure is tempting to chuck Microsoft’s Office and web products and their complicated Enterprise and Select Agreements in favor of open source equivalents. And the software for open source is on the web and freely available for such hackers to view! But this developer community is nebulous.

CIO Business Intelligence
MAY 4, 2022
One does not have to buy new hardware. We license it to the companies where they can run it and see the results themselves. If these are open algorithms, what is the added value that you offer here? Hidary: Firstly, it’s a strength that the algorithms are open. There’s no source code out there.

CIO Business Intelligence
AUGUST 21, 2024
NASA’s Jet Propulsion Laboratory, for example, uses multiagent systems to ensure its clean rooms stay clean so nothing contaminates flight hardware bound for other planets. For example, AI agents use open source intelligence to hunt for movie leaks and piracy across social media and the dark web.

Cloud Musings
SEPTEMBER 14, 2013
Instead of leveraging IT budgets to maintain and upgrade hardware and software, cloud allows responders to devote more IT. Further, removing much of the infrastructure from the supply chain eases the logistics of monitoring and maintaining hardware in an. needed, without the concern of paying for licenses that won’t be used.

Galido
NOVEMBER 29, 2018
Some senior management managers may have concerns about the ability of the cybersecurity team to absorb a larger budget in terms of execution and increased headcount, the only alternative is a clever combination of hardware, software, and few personnel to enforce data loss prevention in a custom methodology. Ice Cream Sandwich.

The Verge
OCTOBER 16, 2020
There are lots of ways to play Game Gear games if you really want to, whether it’s through the 3DS Virtual Console or less official means like the countless open-source emulator handhelds out there. I love the original, but I’d never played this version, and it was a blast to see how it was crammed into the Game Gear hardware.
The Verge
AUGUST 3, 2020
The white paper makes clear that Adobe will need lots of hardware and software support for the system to work effectively. Adobe originally announced Twitter and The New York Times Company as partners, and the CAI specifications will be freely available under an open source license.

Scott Lowe
FEBRUARY 10, 2015
Jason Edelman has posted a self-compiled list of networking projects that are open source ; this is a useful list, so thanks for compiling it Jason! I didn’t think that OpenFlow itself was actually open source (even though there are multiple open source implementations of various OpenFlow products).

Scott Lowe
MAY 17, 2019
Servers/Hardware. The CNCF blog has a great article written by an Alibaba software engineer (Xingyu Chen) on some performance optimizations for etcd that have been contributed back to the open source community. These look interesting, but be aware that they are not licensed with an open source license.
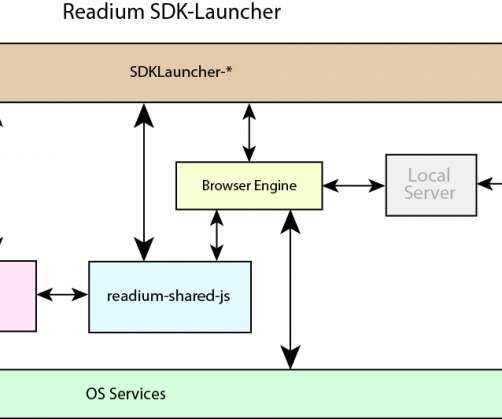
Kitaboo
MAY 19, 2020
The Open Source Foundation aims to develop technology for expediting the adoption of ePUB3 and the Open Web Platform by the Digital Publishing Industry. It strives to deliver leading-edge functionality that is fully specified, free, open, and interoperable. x, audiobooks, Web Pub, and image-based books such as Manga.

Scott Lowe
APRIL 15, 2022
Xavier Avrillier walks readers through using Antrea (a Kubernetes CNI built on top of Open vSwitch—a topic I’ve touched on a time or two) to provide on-premise load balancing in Kubernetes. Servers/Hardware. Cabling is hardware, right? Ulrich Speidel shares some of the findings after the volcanic eruption in Tonga.

Dataconomy
APRIL 24, 2024
Meta made its new Llama 3 LLM open-source and you can run it locally with Ollama. By making Llama 3 open-source, Meta has unlocked a wealth of potential for businesses of all sizes. Ollama provides a platform for running open-source large language models such as Llama 2 on local systems. What does Ollama do?

Scott Lowe
DECEMBER 6, 2013
Here’s a good source. Servers/Hardware. In part 2 , Mike discusses things like using the appropriate virtual hardware, the right kernel modules for VMXNET3, getting rid of unnecessary hardware (like the virtual floppy), and similar tips. Want some additional information on layer 2 and layer 3 services in VMware NSX?
ForAllSecure
JANUARY 21, 2021
Because protocol fuzzers license per test suite, users have access to the test suite for regression testing as well. The quality of results -- defects found as well as test suite -- from open source fuzzers is largely dependent on implementation. Protocol suite licenses are for consecutive use only. Protocol Fuzzing.
ForAllSecure
JANUARY 21, 2021
Because protocol fuzzers license per test suite, users have access to the test suite for regression testing as well. The quality of results -- defects found as well as test suite -- from open source fuzzers is largely dependent on implementation. Protocol suite licenses are for consecutive use only. Protocol Fuzzing.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content