Why traditional malware detection can't stop the latest security threats
Tech Republic Security
MARCH 16, 2021
Isolating your hardware and your applications is a more effective way to prevent malware from infecting your critical endpoints, says HP.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
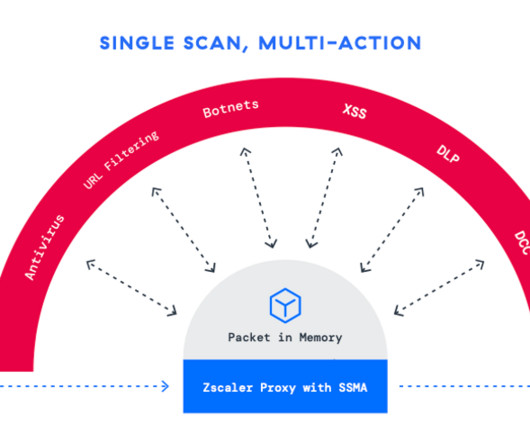
Network World
DECEMBER 20, 2024
Attackers are using encrypted channels to bypass traditional defenses, concealing malware, phishing campaigns, cryptomining/cryptojacking, and data theft within encrypted traffic. Malware dominates the landscape: Malware remains the most prevalent encrypted threat, representing 86.5% Encrypted threats accounted for 87.2%
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Tech Republic Security
FEBRUARY 15, 2024
Whether an infection is the result of a disgruntled employee, hardware vulnerability, software-based threat, social engineering penetration, robotic attack or human error, all organizations must be prepared to immediately respond effectively to such an issue if the corresponding damage is to be minimized.

Tech Republic Security
JANUARY 22, 2023
Whether an infection is the result of a disgruntled employee, hardware vulnerability, software-based threat, social engineering penetration, robotic attack or human error, all organizations must be prepared to immediately respond effectively to such an issue if the corresponding damage is to be minimized.

Tech Republic Security
NOVEMBER 14, 2022
The post Get instant malware filtering with Gryphon Guardian appeared first on TechRepublic. TechRepublic readers can get this tiny mesh router that blocks security threats for only $79.
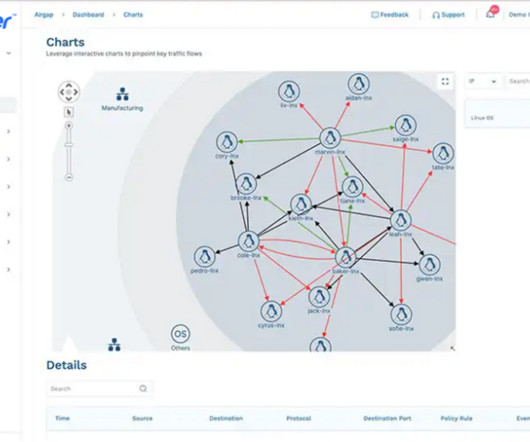
Network World
NOVEMBER 6, 2024
Furthermore, IoT malware attacks have been on the rise. ThreatLabz reported a 45% increase in IoT malware attacks over the past year, with a 12% increase in payload delivery attempts to IoT devices. The manufacturing sector experienced the highest volume of IoT malware attacks, accounting for 36% of all observed blocks.

Network World
JANUARY 28, 2025
The bad news: According to researchers at Lumen Technologys Black Lotus Labs, the unknown attacker can install a reverse shell on the local file system so they can control the router, steal data, or deploy more malware. First, its re-imaging or, in some cases, hardware replacement, depending on the depth of the infection.

CIO Business Intelligence
MARCH 14, 2025
While a firewall is simply hardware or software that identifies and blocks malicious traffic based on rules, a human firewall is a more versatile, real-time, and intelligent version that learns, identifies, and responds to security threats in a trained manner. In the past few months, infostealer malware has gained ground.

Network World
JANUARY 10, 2018
Today Cisco rolled ETA out beyond just the enterprises switches it was originally designed for and made it available on current and previous generation data center network hardware too. MORE AT NETWORK WORLD : What is intent based networking? | Why intent based networking could be a big deal + To read this article in full, please click here

Network World
SEPTEMBER 10, 2021
Called Okyo Garde, the bundle incuds Wi-Fi-6-based hardware and mobile application-security software that includes threat-intelligence updates, and sells the hardware and software to enterprises as a customizable subscription.

Network World
JUNE 11, 2018
The bad news is these vulnerabilities are easily exploitable and can give malware the same effect as having physical access to this kind of system. “A A physical attacker who can open the case could simply attach a hardware programmer to bypass protections.

Tech Republic Security
SEPTEMBER 12, 2023
Check Point's Global CISO discusses the firm's 2023 threat intelligence, including new AI malice and threat actors spreading malware by dropping flash drives.

Network World
FEBRUARY 6, 2025
Three new boxes in the FortiGate G Series portfolio the 70G, 50G, and 30G include integrated firewall, intrusion prevention, malware and ransomware protection, SD-WAN, and switching capabilities, all of which can be managed via the vendors FortiManager centralized management platform.

CIO Business Intelligence
OCTOBER 24, 2024
It can also create cyber threats that are harder to detect than before, such as AI-powered malware, which can learn from and circumvent an organization’s defenses at breakneck speed. Businesses will need to invest in hardware and infrastructure that are optimized for AI and this may incur significant costs.

Tech Republic Security
JULY 20, 2017
Hardware can fail and malware happens to the best of us. Don't be caught without the ability to restore a computer: Use one of these 10 free backup programs instead.

Tech Republic Security
APRIL 28, 2023
Europe and Ukraine are reportedly targets in this malware threat. Learn how to protect affected Cisco routers. The post Threat actor APT28 targets Cisco routers with an old vulnerability appeared first on TechRepublic.

Network World
MAY 22, 2016
These options include both hardware and software approaches IT pros can take to defeat the malware, a group at this weekend’s Security BSides Boston conference was told. One method goes after the droppers that first infect target machines in preparation for downloading the main malware payloads.

Network World
FEBRUARY 20, 2025
Sovereign SASE goes a step further, with Versas SASE software running on customer-owned hardware and environments. The company provides the software and recommends the hardware, but the customer maintains full control over the deployment.

IT Toolbox
AUGUST 11, 2022
Black Hat USA boasts a strong roster, covering themes such as firmware and hardware hacking, zero-day malware discoveries, the most recent APT research, and more. Here’s a look at the event’s top highlights. The post Black Hat USA: Five Highlights from the Top InfoSec Summit of the Year appeared first on Spiceworks.
TechSpot
SEPTEMBER 30, 2022
Chaos is a novel malware written in the Go programming language with pretty unique capabilities. Discovered and analyzed by Black Lotus Labs, the research arm of security company Lumen, the new threat can infect a plethora of computing platforms both on the software and hardware front. There are more than.

Dataconomy
MARCH 21, 2025
Malware has become an omnipresent threat in todays digital landscape, affecting devices, networks, and even entire organizations. Understanding the nature of malware can equip individuals and enterprises with the knowledge needed to defend against its potentially devastating effects. What is malware?

Dataconomy
JANUARY 10, 2025
malware, an infostealer targeting macOS, evades antivirus detection by employing an encryption mechanism drawn from Apple’s XProtect antivirus product. malware uses Apples encryption to evade detection Banshee 2.0 malware uses Apples encryption to evade detection Banshee 2.0 The Banshee 2.0
SecureWorld News
JUNE 24, 2023
This question arises amidst the constant battle against threats posed by malware. By tricking the malware into identifying the environment improperly, security professionals could outsmart self-termination mechanisms utilized by certain strains. Malware employs complex and sophisticated techniques to detect virtualized environments.

CTOvision
JULY 29, 2013
” “The suppliers will provide a centralized way for government agencies to procure hardware, software and consulting services for continuous monitoring and real-time threat detection.” ” The size and import of a hub such as this one should create a very interesting bidding and proposal process.

The Verge
OCTOBER 6, 2021
If you think your PC is infected with some kind of malware or you just want to do a scan as part of a digital cleanup, Windows has a built-in security tool that can help you on your way — no third-party software to install or pay for. After you’ve got it open, here’s some of what you can do: Run a malware scan on Windows 11.

CIO Business Intelligence
OCTOBER 4, 2023
From embedding malware or a phishing link in a document to manipulated or outright forged documents and other types of cyber fraud, the increase in document-related attacks cannot be ignored, especially if your company handles tax forms, business filings, or bank statements–the three types of most frequently manipulated documents.

TechSpot
JANUARY 23, 2025
However, beneath its unassuming exterior lies Buffalo's proprietary "DiXiM Security Endpoint" an embedded anti-malware system that monitors files for threats in real-time. At first glance, the RUF3-KEV looks like an ordinary USB stick. Read Entire Article

CIO Business Intelligence
NOVEMBER 23, 2022
They achieve this via several means, but one of the most common is via phishing, which typically involves convincing someone to download a piece of malware from a legitimate-looking email that will then gather login data and other sensitive info that can give the criminals access to much more within the organisation.

Network World
DECEMBER 10, 2024
Many IoT/OT devices lack integrated security features and/or often operate on outdated hardware and software, resulting in highly vulnerable devices. Cato IoT/OT Security is a native feature in the Cato SASE Cloud Platform , which allows enterprises to activate the new solution without installing or configuring new hardware or software.

CIO Business Intelligence
SEPTEMBER 29, 2023
The process starts with identifying compromised hardware, software, and human assets – both internal and external – by way of scanning and reconnaissance methods. Let’s revisit the most prevalent security threats and see how they’re evolving in 2023.

Tech Republic Security
APRIL 22, 2024
Threats from malware, cryptographic infections and compromised networks have never been greater. Headlines regularly attest to such widespread problems, from infection-felled organizations to dangerous vulnerabilities in popular tools.

CTOvision
FEBRUARY 4, 2014
Secure Configurations for Hardware and Software on Mobile Devices, Laptops, Workstations, and Servers. href="[link] Control 3: Secure Configurations for Hardware and Software on Mobile Devices, Laptops, Workstations, and Servers. Malware Defenses. href="[link] Control 5: Malware Defenses. Application Software Security.

CTOvision
APRIL 11, 2014
Threats to our information are not only from malware or brute force hacks or social engineering. Sometimes we read about very sophisticated attacks against hardware that require advanced engineering. By Bob Gourley. Criminals are motivated to look for every advantage.

TechSpot
AUGUST 31, 2021
As a result, both industries experienced healthy growth, and the hardware industry struggled to keep up with demand for better consoles, The pandemic has had a strong influence over the way we use the Internet, with many more people finding solace during lockdowns by turning to streaming and gaming activities.

SecureWorld News
JANUARY 16, 2025
Strategies for protecting oil and gas infrastructure Regular updates and patching: Outdated software and hardware are the most common entry points for cyberattacks. Lessons learned Segmentation of networks: IT and OT systems must be isolated to prevent malware from spreading.

Network World
FEBRUARY 1, 2017
Macs are really no more secure than a PC, but for many years there just weren’t as many out there because of the expense of the hardware and other issues. The PC attack surface is much wider; therefore, criminals develop malware that works on PCs because the payout is much higher.

CTOvision
OCTOBER 19, 2016
Before connectivity is provisioned, the hardware identity and software hashes from the user’s device are checked. Conceptually the new security stack is a hardware-based virtual enclave. For example, enclave access requires a valid hardware token, certificate exchange and device verification all to be approved in the same connection.

The Verge
FEBRUARY 24, 2022
A tool released on GitHub advertised the sought-after ability to unlock the full Ethereum mining capabilities of recent Nvidia RTX graphics cards but actually contains malware. Importantly, according to Tom’s Hardware , the tool doesn’t even perform its namesake function of removing the cap on the hash rate for your GPU.

SecureWorld News
APRIL 7, 2022
Cyclops Blink was a two-tiered global botnet of thousands of infected network hardware devices, according to the DOJ. The DOJ discusses the operation in a recent statement: "The operation copied and removed malware from vulnerable internet-connected firewall devices that Sandworm used for command and control (C2) of the underlying botnet.

SecureWorld News
DECEMBER 27, 2021
Prosecutors say he was one of the masterminds behind bribing AT&T Wireless employees to install both malware and hardware in this Washington call center. Employees installed malware. ". Employees installed new variants of malware. What, exactly, was this unlocking malware all about?
The Verge
JUNE 25, 2021
It’s a significant hardware change that has been years in the making, but Microsoft’s messy way of communicating this has left many confused about whether their hardware is compatible. TPMs work by offering hardware-level protection instead of software only. What is a TPM, and why do you need one for Windows 11 anyway?

CTOvision
AUGUST 4, 2015
For organizations that do not have an existing security solution, the Verisign DNS Firewall provides a service that secures your traffic navigation without the significant cost burden associated with hardware implementations.

CIO Business Intelligence
JUNE 7, 2022
One example is the ability to identify words or phrases used by malware bots. To create a productive, cost-effective analytics strategy that gets results, you need high performance hardware that’s optimized to work with the software you use. Another use of NLP tools is to investigate and combat fraud.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?



Let's personalize your content