How to implement mindful information security practices
Tech Republic Security
JANUARY 8, 2021
Mindfulness is all about being aware, so why not incorporate that in your cybersecurity practices?
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Tech Republic Security
JANUARY 8, 2021
Mindfulness is all about being aware, so why not incorporate that in your cybersecurity practices?

Network World
APRIL 26, 2017
Just use Google to learn how to access the Dark Web, and you can find hackers who, for a price, are more than happy to write malware, create highly effective spear phishing campaigns and develop bogus websites for harvesting login credentials. Also on Network World: DDoS-for-hire services thrive despite closure of major marketplace +.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Network World
OCTOBER 21, 2024
There’s been a lot of talk over the past few years about a shortage of skilled cybersecurity talent , but from where we sit at the NYC DOE Division of Information and Instructional Technology (DIIT), we see budding security pros all around us. It’s been our privilege to foster the next generation of cybersecurity professionals.

Tech Republic Security
JUNE 21, 2024
Immersing yourself in best practices for ethical hacking, pen-testing and information security can set you up for a career or better-protected business.

CIO Business Intelligence
NOVEMBER 27, 2024
A hybrid approach often offers the best solution, allowing organizations to store and process sensitive information securely on-premises while leveraging the scalability and flexibility of the cloud for less critical workloads.

Information Week
MARCH 14, 2024
Chief information security officers are on the job hunt. What should they be looking for in an offer?

CIO Business Intelligence
OCTOBER 31, 2023
There’s a security issue.” That’s why Discover® Financial Service’s product security and application development teams worked together to shift security left by integrating security by design and conducting early security testing often to identify vulnerabilities prior to hitting deployment.

CIO Business Intelligence
APRIL 1, 2025
The promised land of AI transformation poses a dilemma for security teams as the new technology brings both opportunities and yet more threat. 1] It is beyond human capabilities to monitor and respond to these attacks; it is also putting immense stress on security teams. Security technicians need to harness the power of AI.

CIO Business Intelligence
APRIL 2, 2025
Several hospitals canceled surgeries as well, and banks, airports, public transit systems, 911 centers, and multiple government agencies including the Department of Homeland Security also suffered outages. Customers also got additional controls over how updates are deployed. What if theres an urgent security fix?

IT Toolbox
FEBRUARY 22, 2024
Learn how CISOs (chief information security officer) can leverage financial metrics to communicate cybersecurity success effectively to the board. The post 3 Metrics CISOs Should Present to the Board and How to Calculate Them appeared first on Spiceworks.

CTOvision
MARCH 25, 2020
Johnson explain how SaaS companies can secure customer data on Help Net Security : Recently, some of the biggest names in SaaS have experienced customer support data breaches. Read Robert C.

Network World
APRIL 25, 2017
There are two times you might have to talk to your organization’s board of directors about security: before a breach and after. That should mean the board wants to talk with you, the CISO, to learn firsthand what your department is doing to mitigate information security threats.

CIO Business Intelligence
JULY 25, 2024
The already heavy burden born by enterprise security leaders is being dramatically worsened by AI, machine learning, and generative AI (genAI). Information security leaders need an approach that is comprehensive, flexible and realistic. Enterprise security leaders can start by focusing on a few key priorities.

CIO Business Intelligence
NOVEMBER 18, 2024
Simultaneously, the monolithic IT organization was deconstructed into subgroups providing PC, cloud, infrastructure, security, and data services to the larger enterprise with associated solution leaders closely aligned to core business functions. They see a product from beginning to end and it’s pretty rewarding.”

CIO Business Intelligence
OCTOBER 24, 2024
One key reason is that CIOs and chief information security officers (CISOs) are not always aligned in how to enable productive, secure work. But in practice, IT and security teams often work separately, without common knowledge, data, goals, priorities, and practices. Unlock data silos.

Information Week
SEPTEMBER 4, 2018
Director, Information Security at First National Technology Solutions, shares examples of how to apply your existing IT tools to work for your cloud security strategy. Robert LaMagna-Reiter, Sr.

CIO Business Intelligence
MAY 27, 2024
If there is a single theme circulating among Chief Information Security Officers (CISOs) right now, it is the question of how to get stakeholders on board with more robust cybersecurity training protocols. Human error remains one of the leading causes of security breaches.

CIO Business Intelligence
SEPTEMBER 7, 2023
Slowing the progression of AI may be impossible, but approaching AI in a thoughtful, intentional, and security-focused manner is imperative for fintech companies to nullify potential threats and maintain customer trust while still taking advantage of its power.

CIO Business Intelligence
APRIL 6, 2022
will offer insights on designing hybrid cloud environments for security and flexibility. Shamim Mohammad, EVP and chief information and technology officer at CarMax , will present a case study on how the cloud enables the company’s signature “Instant Offer” feature. And hear how the U.S.

CIO Business Intelligence
DECEMBER 20, 2024
As concerns about AI security, risk, and compliance continue to escalate, practical solutions remain elusive. the early days of AI deployment, there was no well-known incident equivalent to the 2013 Target breach that represented how an attack might play out. The latter issue, data protection, touches every company.

Network World
MARCH 13, 2017
Multiple times each year, LinkedIn feeds and information security forums light up with examples of the latest and greatest versions of phishing attacks. This article on W-2 scams sprung from a conversation I had with my colleague Steve Williams, who ended up being my co-author. Check out more about him at the end of this piece.

CIO Business Intelligence
AUGUST 23, 2024
INE Security , a global cybersecurity training and certification provider, recently launched initiatives with several higher education institutions in an ongoing campaign to invest in the education of aspiring cybersecurity professionals.

Network World
JUNE 14, 2016
With use cases to gather analytics around data, networks and user behaviors, there are endless possibilities for utilizing this information. But, when looking to drill down this data to inform security decisions, is a massive amount of information, which could include fall positives, really that useful?

CIO Business Intelligence
FEBRUARY 11, 2025
After more than a decade leading the digital transformation and cybersecurity initiatives of the services company, hes managed to forge a synergy where tech and information security are established as fundamental pillars for business success. Another vertical of the plan is closely related to Industry 4.0

Network World
DECEMBER 29, 2016
The high-water line in information security gets higher each year. Just as we think we’ve finally figured out how to defend against attacks, then attackers come up with something new and we are right back to trying to figure out what to do next. For example, ransomware has surged in the last year.

CTOvision
DECEMBER 19, 2014
The White House declares it’s a national security issue and leaks intelligence that North Korea is behind the attack. Most corporate hacks we see are focused on either customer data (credit cards, medical records, social security numbers, passwords, bank account information, email addresses) or company proprietary documents.

CTOvision
MAY 22, 2014
Organizations are giving more priority to development of information security policies, as protecting their assets is one of the prominent things that needs to be considered. So an organization makes different strategies in implementing a security policy successfully. Security policies are tailored to the specific mission goals.

Network World
MAY 31, 2016
Employees are often considered the weakest link in organizations' efforts to create a strong security posture. Even organizations with security awareness programs in place struggle to instill strong security behaviors.

CIO Business Intelligence
AUGUST 15, 2024
Most IT and information security leaders are very familiar with the term VUCA. Our conversation touched on what defines a great information security leader today and how those leadership attributes fuel results for the business. All they want to know is how to solve the problem.”
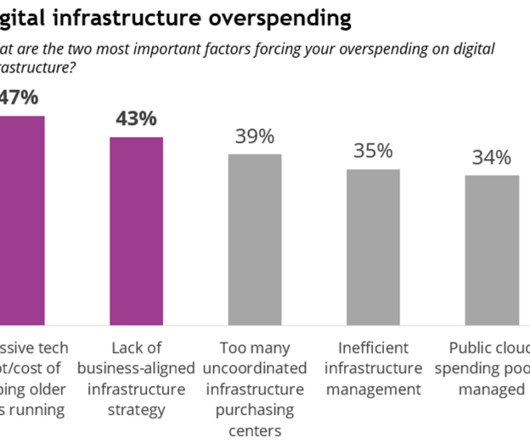
CIO Business Intelligence
AUGUST 1, 2024
Looking ahead to the next 12-18 months, two top priorities emerge for IT leaders: developing a strong business case for AI infrastructure spending (cited by 35% of respondents to IDC’s Future Enterprise Resiliency and Spending Survey, Wave 3 , March 2024) and increasing cyber resilience and security (34%).

CIO Business Intelligence
APRIL 18, 2023
Other responsibilities may include addressing digital transformation initiatives, guiding application development, and identifying security issues. The role can be particularly appealing for semi-retired and financially secure CIOs who wish to remain active in IT without the angst and drama that often surrounds C-level politics.

Network World
AUGUST 4, 2016
At the Black Hat conference in Las Vegas, CSO’s Steve Ragan chats with Steven Grossman of Bay Dynamics about how companies can survive the avalanche of information security hype and buzzwords when speaking with vendors who are promising everything.

CIO Business Intelligence
MAY 24, 2024
A variety of roles in the enterprise require or benefit from a GRC certification, such as chief information officer, IT security analyst, security engineer architect, information assurance program manager, and senior IT auditor , among others. Is GRC certification worth it?

CIO Business Intelligence
SEPTEMBER 23, 2022
The practice brings together formerly separate disciplines of information security, business continuity, and disaster response (BC/DR) deployed to meet common goals. With a risk-based approach to cyberresilience, organizations evolve practices and design security to be business-aware. The HPE GreenLake Advantage.

CIO Business Intelligence
MARCH 30, 2022
Despite much discussion about how to icrease the percentage of women in cybersecurity roles over the last decade, women make up only 25% of the global cybersecurity workforce, according to the latest (ISC)² Cybersecurity Workforce Study.

CIO Business Intelligence
JULY 13, 2022
Shadare, along with Orca Security advisory CISO Andy Ellis and Spire Security Vice President of Research Pete Lindstrom, will share cybersecurity metrics that matter as part of CSO’s Future of Cybersecurity Summit , taking place virtually July 19-20. One risk mitigation strategy is to move away from passwords to more secure protocols.

CIO Business Intelligence
SEPTEMBER 12, 2023
Over 100,00 organizations are expected to be impacted by Network and Information Security Directive (NIS2) cybersecurity standards that European Union (EU) member states must implement by October 2024. [i] This concept of least-privilege access is fundamental to Zero Trust Security practices.

Forrester IT
JUNE 8, 2018
If you had half an hour with a board member, and you wanted to get coaching from them about how to communicate with them about security, what would you ask them? In a few weeks’ time, I will have just that opportunity when I facilitate a panel with some prominent board directors. Getting inside the […].

CIO Business Intelligence
JULY 25, 2024
To succeed, you need to understand the fundamentals of security, data storage, hardware, software, networking, and IT management frameworks — and how they all work together to deliver business value. This certification will show you’re capable of dealing with any security threats, and well-versed on the requirements for IT governance.

Network World
SEPTEMBER 21, 2016
Given the vast and increasing volumes of data within organizations today, securing your data can seem an insurmountable task. But you can get your arms around it if you assess the value of your data and focus your attention on protecting your mission-critical information assets — the crown jewels.

Network World
JANUARY 29, 2025
From the editors of our sister publication CSO, this enterprise buyers guide helps network security staff understand what SIEM can do for their organizations and how to choose the right solution.

CTOvision
FEBRUARY 20, 2014
Recognized as a pioneer in the field of classified information protection, Mr. Bigman developed technical measures and procedures to manage the nation’s most sensitive secrets. Bigman worked in every area of information and data security, the last fifteen years as the Agency’s Chief Information Security Officer (CISO).

CIO Business Intelligence
SEPTEMBER 22, 2022
Two years on since the start of the pandemic, stress levels of tech and security executives are still elevated as global skills shortages, budget limitations and an ever faster and expanding security threat landscape test resilience. “In We need to remember that it’s not just about technology,” she says. “It It involves people too.”.

CIO Business Intelligence
OCTOBER 27, 2023
The follow-on Apple Deployment and Management course focuses on configuring, managing, and securing Apple products using mobile device management (MDM). The exam covers topics such as coding, designing cloud architecture, cloud security, troubleshooting, implementation, migration, load and performance testing, and business applications.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content