How to Create and Use a Docker Secret From a File (+Video)
Tech Republic Security
SEPTEMBER 19, 2023
Learn how to create and use a Docker secret from a file for secure storage of sensitive data with this step-by-step tutorial.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Tech Republic Security
APRIL 7, 2022
If you work on headless Linux servers, you might want to have a command-line password storage tool. Jack Wallen shows you how to use GnuPG and pass for this purpose. The post How to safely store passwords on a Linux server appeared first on TechRepublic.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

CIO Business Intelligence
DECEMBER 10, 2024
Kubernetes Kubernetes is an open-source automation tool that helps companies deploy, scale, and manage containerized applications. Tableau allows users to extract and organize data, while also offering aesthetics to help communicate the data to others outside of the data analyst team.

CIO Business Intelligence
MAY 9, 2023
Tap into open-source software Mainframe-dependent businesses often think that open source is just for cloud-based products – but that assumption is incorrect. Open-source software accelerates IBM Z® application development and delivery through modern tools that drive automation and integration to and from the mainframe.

Tech Republic Cloud
APRIL 13, 2023
If you're either transitioning to Podman or are new to container development, Jack Wallen shows you how easy it is to deploy a container with persistent storage. The post How to deploy a Podman container with persistent storage appeared first on TechRepublic.

CIO Business Intelligence
JANUARY 20, 2023
2] Foundational considerations include compute power, memory architecture as well as data processing, storage, and security. The most innovative unstructured data storage solutions are flexible and designed to be reliable at any scale without sacrificing performance.
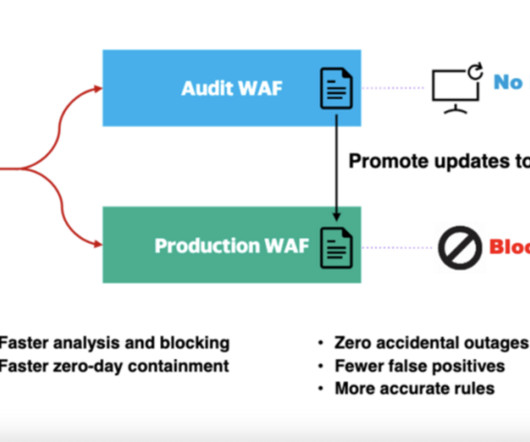
CIO Business Intelligence
JULY 17, 2023
This can occur due to insecure configurations, inadequate access controls, or vulnerabilities in cloud storage or databases. Attackers may upload malicious files or applications to cloud storage or use cloud infrastructure to propagate malware to unsuspecting users. What can businesses do?

CIO Business Intelligence
AUGUST 8, 2024
In addition to swapping out expensive commercial models for open source ones, or small language models (SLMs), KPMG is also experimenting with alternatives to traditional AI processing hardware. There’s the cost of storage, development, and running the application,” says Chandrasekaran. But there are similarity techniques.”

CIO Business Intelligence
DECEMBER 3, 2024
These different databases have varying licensing mechanisms, including traditional, cloud, full open source, and commercial open source. 1] Between storage, compute, and data transfer costs, plus backups and snapshots, use of the cloud can drive up database costs if not properly managed. Expansion of license types.

CIO Business Intelligence
APRIL 10, 2024
With the potential to incur high compute, storage, and data transfer fees running LLMs in a public cloud, the corporate datacenter has emerged as a sound option for controlling costs. But IT leaders shouldn’t have to pretend to be Sherlock Holmes to figure out how to run them cost-effectively while delivering the desired outcomes.

CIO Business Intelligence
FEBRUARY 12, 2024
Such bleak statistics suggest that indecision around how to proceed with genAI is paralyzing organizations and preventing them from developing strategies that will unlock value. Prepare the data through anonymizing, labeling and normalizing across data sources and create guardrails for governance, quality, integrity and security.

CIO Business Intelligence
JUNE 14, 2023
Organization: INFORMS Price: US$200 for INFORMS members; US$300 for nonmembers How to prepare: A list of study courses and a series of webinars are available through registration. Organization: AWS Price: US$300 How to prepare: Amazon offers free exam guides, sample questions, practice tests, and digital training.

Tech Republic
OCTOBER 11, 2022
The post How to deploy ownCloud collaboration suite with persistent storage using Docker appeared first on TechRepublic. Jack Wallen walks you through the process of quickly deploying the ownCloud file-sharing and collaboration platform with the help of Docker.

CIO Business Intelligence
MAY 12, 2022
As well as a clear understanding of how to take full advantage of it in real-time. How important is open source software and the innovation it provides? Open source is very important, and I believe it’s a key way to accelerate innovation.

CIO Business Intelligence
APRIL 25, 2022
As a result, data scientists often spend too much time on IT operations tasks, like figuring out how to allocate computing resources, rather than actually creating and training data science models. And PowerScale F600 or H600 provides highly scalable storage. IDC agrees. A partial solution lies in the adoption of MLOps.

CIO Business Intelligence
APRIL 25, 2022
In an earlier article , I discussed three proven ingredients for a holistic data platform approach to managing and harnessing data – cloud-native technologies, real-time data, and open source software(OSS) – to drive business value. Let’s look at how to do this. LoBs should be empowered with easy access to data streams.

Dataconomy
FEBRUARY 21, 2020
Delta Lake is an open-source storage layer that solves many concerns around data. The post How to make data lakes reliable appeared first on Dataconomy. High quality, reliable data forms the backbone for all successful data endeavors, from reporting and analytics to machine learning.

CIO Business Intelligence
APRIL 25, 2024
With questions around ROI, increasing outlay, and corporate scrutiny on IT cost savings on the rise, CIOs must know not only what contributes to their organization’s overall cloud spend but also how to optimize it. And that’s all before considering the need to fuel new AI initiatives , which can push cloud costs up further.

Scott Lowe
NOVEMBER 27, 2024
Cloud Computing/Cloud Management Luc van Donkersgoed explains how he optimized caching for his AWS News site to improve performance. The AWS open source newsletter is always a great source of information; check out issue #204. Similarly, the AWS Cloud Security weekly newsletter is another great source of information.

Dataconomy
MAY 10, 2023
Open source business intelligence software is a game-changer in the world of data analysis and decision-making. With open source BI software, businesses no longer need to rely on expensive proprietary software solutions that can be inflexible and difficult to integrate with existing systems.

SPF13
MAY 14, 2012
How to build a e-commerce product that: 1. is a scalable, high-performance, open source document database written in C++. s how to install it. The following example will show you how to connect to a Mongo DB server, create a db and a collection and insert a single record into that collection. Open source.

The Accidental Successful CIO
AUGUST 14, 2013
It turns out that there is another problem that has arrived at the same time and right now there is not a clear answer to how best to deal with it: how to back up all of that data. Blue Elephant Consulting – Your Source For Real World IT Department Leadership Skills™. What’s The Big Deal Here? Dr. Jim Anderson.

CIO Business Intelligence
JANUARY 19, 2024
You need to be skilled in deploying and managing resources, managing identities and governance, implementing and managing storage, and configuring and managing virtual networks. It covers programming skills; managing and improving data; transforming, accessing, and manipulating data; and how to work with popular data visualization tools.

Dataconomy
JUNE 27, 2018
Data science has gone through a rapid evolution, fueled by powerful open source software and more affordable and faster data storage solutions. This evolution opens new and innovative pathways for many. The post Four Data Analytics Pitfalls and How to Avoid Them appeared first on Dataconomy.

Tech Republic
APRIL 6, 2022
If you need persistent storage for your Docker containers, Jack Wallen believes there's no easier way to create them than with Portainer. Read on to find out how to create both local and remote volumes with ease. The post How to create a persistent volume for your container deployments with Portainer appeared first on TechRepublic.

CIO Business Intelligence
MARCH 29, 2022
An even larger issue is that people may not know how to see value in data. But to get the benefits data has to offer, you must learn to use it, just like you need to know how to use exercise equipment before it can do you any good. . One new initiative is the Agstack Foundation , an open-source digital infrastructure for agriculture.

CIO Business Intelligence
AUGUST 14, 2024
But those close integrations also have implications for data management since new functionality often means increased cloud bills, not to mention the sheer popularity of gen AI running on Azure, leading to concerns about availability of both services and staff who know how to get the most from them.

Dataconomy
OCTOBER 9, 2017
Image: SAP Cloud Platform Hadoop is a Java-based, open source framework that supports companies in the storage and processing of massive data sets. The post How to best Leverage the Services of Hadoop Big Data appeared first on Dataconomy. Even so, it’s.

Network World
DECEMBER 10, 2024
From the judge The challenge for SASE vendors is how to integrate multiple features and functions. The VP80ES is a powerful data storage solution that represents a one-stop shop for small and medium-sized businesses, with its 8TB drive costing a fraction of similarly capable models.

Linux Academy
JANUARY 1, 2020
How to Get a Linux Job. Learn how to use the keyboard to work with your text documents, complete searches, replace text, and format. Learn how to use the keyboard to work with your text documents, complete searches, replace text, and format. Azure Cloud Services and Infrastructure. Included with Community Membership.

SPF13
OCTOBER 28, 2012
While Hadoop is the most well-known technology in big data, it’s not always the most approachable or appropriate solution for data storage and processing. In the past few years open source has made Big Data accessible to the rest of us. How to deliver a great conference tutorial. Scalable, inexpensive storage.

SPF13
OCTOBER 28, 2012
While Hadoop is the most well-known technology in big data, it’s not always the most approachable or appropriate solution for data storage and processing. In the past few years open source has made Big Data accessible to the rest of us. How to deliver a great conference tutorial. Scalable, inexpensive storage.
Kitaboo
OCTOBER 29, 2020
Book digitization has reduced the need for creating physical storage facilities while protecting books against any substantial wear and tear. Step 4 – Save the scanned file as a PDF or convert it into an ebook by using open source software. How can publishing face-up the mobile challenge?

CIO Business Intelligence
APRIL 8, 2022
Yesterday’s challenge: Lack of power, storage, and data. That’s because companies didn’t have sufficient computing power, storage capabilities, or enough data to make an investment in developing ML and AI models worthwhile. Today’s challenge: Model building is complicated.

SecureWorld News
FEBRUARY 19, 2024
WordPress sites can be structured in an almost infinite number of ways, integrating with numerous other open-source plugins and third-party systems. Choose secure hosting providers and plugins Your web hosting provider controls physical hardware, sensitive data storage, and network configurations.

Linux Academy
JANUARY 30, 2020
How to Get a Linux Job. Learn how to use the keyboard to work with your text documents, complete searches, replace text, and format. Learn how to use the keyboard to work with your text documents, complete searches, replace text, and format. AWS Cloud Services and Infrastructure – Cost Optimization Deep Dive. LXC/LXD Deep Dive.

CIO Business Intelligence
JANUARY 31, 2024
He also recommends tapping the open-source community for models that can be pre-trained for various tasks. AWS also has models to reduce data processing and storage, and tools to “right size” infrastructure for AI application. Our theory is no. All those 13,000 new models didn’t require any pre-training,” he says.

Galido
FEBRUARY 1, 2019
Information Technology Blog - - How To Reduce IT Costs - Information Technology Blog. It can help to reduce IT costs by eliminating the need for expensive storage and hardware kept on-site. Use Open Source Software. The post How To Reduce IT Costs appeared first on Information Technology Blog.
Linux Academy
APRIL 10, 2020
By now you’ve heard the stories that Microsoft loves Linux and fully embraces the open-source world. Microsoft, under Satya Nadella, has taken a new stance on open-source , which to some is a complete flip-flop from the Microsoft of the past. Visual Studio Code. TypeScript.NET Core. and many more.

The Verge
NOVEMBER 6, 2020
For all your other desktop software needs, there’s usually a free, open-source program that can do just as good a job. But for our purposes, I’m going to tell you how to install Linux Mint. First, I’ll show you how to try Mint out, then how to install it on your machine. Gimp , for example, instead of Photoshop.
Tech Republic Big Data
OCTOBER 11, 2023
In this How to Make Tech Work tutorial, Jack Wallen shows how to create a Docker volume that can be used for any number of containers.

Scott Lowe
NOVEMBER 30, 2012
About a week ago, I published an article showing you how to use EncFS and BoxCryptor to provide client-side encryption of Dropbox data. The Dropbox iOS client still does not, unfortunately, know how to get the Markdown files into Byword. Interoperability Macintosh Security Storage Encryption OSS Privacy'

Scott Lowe
SEPTEMBER 13, 2012
The speaker for the session is Vin Sharma, who helps lead open source software strategies at Intel. The focus of this session, as you can tell from the title, is on security and trust (presumably talking about how to leverage Intel TXT with OpenStack). Sharma reviews again some of the ODCA cloud computing usage models.

Linux Academy
DECEMBER 1, 2019
How to Get a Linux Job. Learn how to use the keyboard to work with your text documents, complete searches, replace text, and format. Learn how to use the keyboard to work with your text documents, complete searches, replace text, and format. Kubernetes The Hard Way. Included with Community Membership. Free Mastery Courses.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?



Let's personalize your content