How to use the Whonix advanced security and privacy distribution
Tech Republic Security
JUNE 19, 2020
Whonix is a Linux desktop dedicated to absolute security and privacy. Find out how to use this unique take on the desktop operating system.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Tech Republic Security
JUNE 19, 2020
Whonix is a Linux desktop dedicated to absolute security and privacy. Find out how to use this unique take on the desktop operating system.

Tech Republic Security
DECEMBER 14, 2021
Qubes OS defines itself modestly as "a reasonably secure operating system." It might actually be one of the safest operating systems, often used by pros who are most concerned with computer security.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Tech Republic Security
JULY 14, 2020
Whonix is a Linux desktop dedicated to absolute security and privacy. Find out how to use this unique take on the desktop operating system.

Network World
DECEMBER 16, 2024
The Tech+ certification covers basic concepts from security and software development as well as information on emerging technologies such as artificial intelligence, robotics, and quantum computing. Infrastructure: Learn how to install common peripheral devices to a laptop or a PC and how to secure a basic wireless network.

Network World
OCTOBER 15, 2024
When deployed properly, SASE, which combines SD-WAN with cloud-delivered security via SSE, enables all users and devices, regardless of location, to securely access an organization’s hybrid network. The best SASE solutions can extend security protections to the microbranch via access points (APs).

Network World
APRIL 4, 2022
Fortinet has made available a new release of its core FortiOS software that includes features the vendor says will help enterprises more tightly meld security and networking controls. How to choose an edge gateway. FortiOS is the vendor’s operating system for the FortiGate family of hardware and virtual components.

Network World
SEPTEMBER 26, 2019
Cisco this week warned its IOS and IOS XE customers of 13 vulnerabilities in the operating system software they should patch as soon as possible. All of the vulnerabilities – revealed in the company’s semiannual IOS and IOS XE Software Security Advisory Bundle – have a security impact rating (SIR) of "high".

Network World
NOVEMBER 12, 2024
“We have gone from choosing an operating system to being able to run any application anywhere and on any cloud by virtualizing storage.” Computing, networks, storage and security management used to operate in silos,” Baguley said. At VMworld Explore, spokespersons tried to dispel the negative publicity. “I

CIO Business Intelligence
APRIL 2, 2025
Several hospitals canceled surgeries as well, and banks, airports, public transit systems, 911 centers, and multiple government agencies including the Department of Homeland Security also suffered outages. Customers also got additional controls over how updates are deployed. What if theres an urgent security fix?

Anoop
MARCH 18, 2020
Let’s check how to create AppLocker Policies to Secure Windows Environments. Introduction Applocker is introduced with the Windows 7 operating system, Windows Server 2008 R2. Subscribe YouTube Channel [link]. and Facebook Page to get latest updates. If you need to prevent an application from running, […].

SecureWorld News
JANUARY 13, 2025
Here's how to build yours. Compliance frameworks like NIST Cybersecurity Framework, ISO 27001, and SOC 2 help shape how businesses prioritize security. And don't overlook risk managementit's all about spotting potential threats and figuring out how to handle them before they become a problem. What is a talent stack?
Tech Republic Security
JUNE 6, 2022
Learn about the new features available with iOS 16, and how to download and install the latest version of Apple’s mobile operating system. The post iOS 16 cheat sheet: Complete guide for 2022 appeared first on TechRepublic.

Network World
MARCH 5, 2025
As organizations grapple with exponential data growth and complex hybrid cloud environments, IT leaders and professionals who can effectively manage, optimize and secure data storage are indispensable, says Gina Smith, research director at IDC and lead for its IT Skills for Digital Business practice. Price: $150 Exam duration: 1.5

Network World
MAY 16, 2024
Kyndryl is targeting new AI, mainframe modernization, and security services in the coming months as it looks to build out its Bridge infrastructure integration platform. Bridge is one of Kyndryl’s major services offerings, which include consulting, hybrid cloud, security, and applications services.
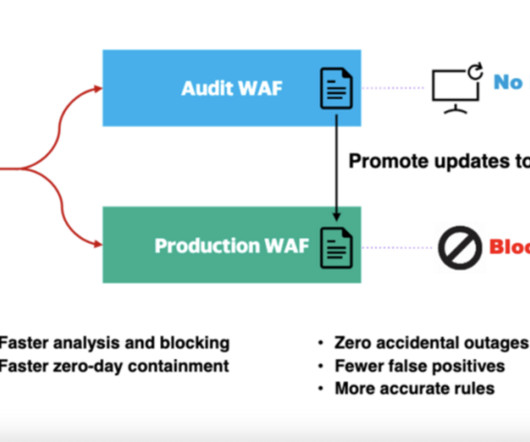
CIO Business Intelligence
JULY 17, 2023
However, this shift requires a thorough understanding of the security implications and how a business can protect its data and applications. As with all technology introductions, it’s important to have clear security policies, tools, processes, and training. How is the cloud being attacked and why? Watch on-demand here.

CIO Business Intelligence
JANUARY 20, 2023
By Anand Oswal, Senior Vice President and GM at cyber security leader Palo Alto Networks Connected medical devices, also known as the Internet of Medical Things or IoMT, are revolutionizing healthcare, not only from an operational standpoint but related to patient care. Many connected devices ship with inherent vulnerabilities.
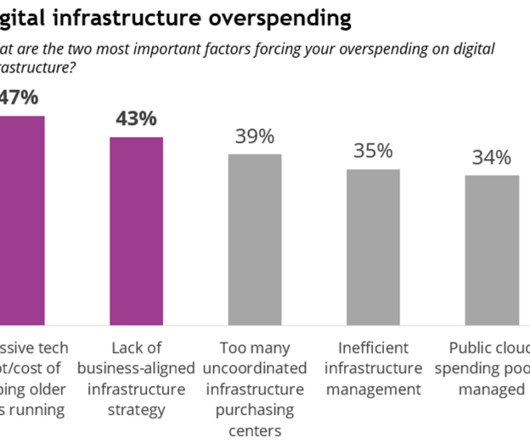
CIO Business Intelligence
AUGUST 1, 2024
Looking ahead to the next 12-18 months, two top priorities emerge for IT leaders: developing a strong business case for AI infrastructure spending (cited by 35% of respondents to IDC’s Future Enterprise Resiliency and Spending Survey, Wave 3 , March 2024) and increasing cyber resilience and security (34%).

Network World
JUNE 8, 2016
A Chromebook is already an ultra-secure computer straight out of the box. Since it doesn’t run a traditional operating system and takes advantage of various Google-powered security measures, Chrome OS is well-guarded against all the miscreants lurking out there on the Web.

Tech Republic Security
AUGUST 4, 2016
A step-by-step guide on how to download, install, and start using Tails, the world's most secure platform.

Network World
MARCH 9, 2017
Developers have embraced Docker containers on public clouds because they don’t need help from an IT operations team to spin them up. A software container is simply a thin package of an application and the libraries that support the application, making it easy to move a container from one operating system to another.

Network World
OCTOBER 15, 2024
So, you may have an edge node with two NICs, VLANs , SR-IOV , and Edge Image Builder understands how to do that.” An organization could build out a single Kubernetes image for its edge deployments and shoot it out to 10,000 systems, for example. how governance has changed, and what to expect next. Wireshark 4.4

CIO Business Intelligence
MAY 26, 2023
It’s a solid choice as an entry-level certification that is well-regarded in the industry and will verify that you have the skills to troubleshoot and resolve problems around networking, operating systems, mobile devices, and security. To earn the certification, you’ll need to pass two exams.

CTOvision
MAY 6, 2014
Microsoft acknowledged a zero day vulnerability in Internet Explorer – the default web browser for many computers, laptops, and tablets – in a security advisory released last weekend. The advisory states that Microsoft will issue a patch in an upcoming security update, after completing its investigation into the matter.

CIO Business Intelligence
OCTOBER 27, 2023
The follow-on Apple Deployment and Management course focuses on configuring, managing, and securing Apple products using mobile device management (MDM). The exam covers topics such as coding, designing cloud architecture, cloud security, troubleshooting, implementation, migration, load and performance testing, and business applications.

CIO Business Intelligence
OCTOBER 20, 2023
It was established in 1978 and certifies your ability to report on compliance procedures, how well you can assess vulnerabilities, and your knowledge of every stage in the auditing process. According to PayScale, the average salary for a CISSP certification is $126,000 per year.

Network World
DECEMBER 10, 2024
But networking vendors are constantly innovating to keep pace with skyrocketing volumes of traffic that need to move securely and reliably across complex multicloud environments. Gluwares approach allows organizations to implement self-operating network capabilities in just three monthsand see ROI within a year.

Tech Republic
JULY 14, 2024
SELinux stands for Security-Enhanced Linux. It is a Linux kernel security model that provides a hardened set of access control security policies for the Linux operating system. SELinux tends to get a bad rap, because it often seems to go out of its way to prevent legitimate applications from working.

CTOvision
SEPTEMBER 16, 2016
We help enterprises build action plans to mitigate risks and improve their security posture. Every person with a computer or phone has information at risk and should take personal responsibility for improving their security posture. Know what https is and how to spot it in your browser. Don’t use free email from your ISP.

Kitaboo
JUNE 25, 2020
Compatible with Multiple Operating Platforms: iOS, Windows and Android are some of the popular operating systems used by most users. If your content can be accessed on just one operating system, you lose out on the other readers. So, look for a software which will help you publish on multiple operating systems.

CIO Business Intelligence
APRIL 7, 2025
While legacy systems can be costly to maintain and be vulnerable to security risk, thats not always the case, he says. Newer, more modern systems may also have their downsides, such as becoming overly burdensome, outliving their usefulness too quickly, and needing to be replaced, Miears says.

Network World
OCTOBER 10, 2024
So, there’s a race on right now for what company will be the default platform for generative AI, the operating system for the next evolution of the enterprise, the middleware that will tie it all together. It makes generative AI tools more accurate, more up-to-date, and can give them access to private information in a secure way.

GeekWire
DECEMBER 18, 2024
A lot has changed since Windows debuted in 1985 as a graphical operating environment which runs on the Microsoft MS-DOS operating system. They noted that more than 500 software developers were planning to build applications for the fledgling operating system. But the first steps into the AI era have been shaky.

Kitaboo
OCTOBER 7, 2021
As a digital publisher, if you too have been facing a similar problem, here is a list of some major author platforms that you can employ to publish your content securely. Using DRM protection to help publishers create and distribute content, KITABOO ensures that safety and security remain the fundamental pillars of your digital space.

Linux Academy
MAY 31, 2019
This week, we’re discussing secure configurations, and why they matter. Our friends at the Center for Internet Security (CIS) listed “Secure Configurations” as the No. 5 most important security control on this year’s Top 20 hit list. Of course, I need to securely configure my devices.

CTOvision
MARCH 12, 2015
How to turn your old phone into a basic PC with less than $25 (ewtnet.com). The Greatest Threat to Smartphone Security: Your 6-Year-Old? Gadgets News Android (operating system) Apple Inc. Read more about WonderCube on gizmag. Related articles. First Apple and Android dual-charger smashes fundraising goal (wired.co.uk).

CIO Business Intelligence
OCTOBER 8, 2024
There is no way it will ever be secure. You need to explain in great detail what it is and what it does, and identify business use cases for how it can be leveraged to better your organization, BEFORE you’ve even touched it! The premise here is to learn how to leverage emerging technology to benefit your organization.

CTOvision
AUGUST 15, 2013
By BryanHalfpap Wireless security is all about implementation. The vendors implementation of the stack, the implementation of the security protocol standards in your OS that you have deployed to your users, the ways that the radios work, and the settings you’ve chosen for your network. How do I test my vulnerability to this?

Scott Lowe
NOVEMBER 27, 2024
Security Ofek Itach and Yakir Kadkoda discuss a security vulnerability in AWS CDK that could—under the right conditions—allow an attacker to gain administrative access to an AWS account. Similarly, the AWS Cloud Security weekly newsletter is another great source of information. Neat stuff.

The Verge
NOVEMBER 6, 2020
But for our purposes, I’m going to tell you how to install Linux Mint. First, I’ll show you how to try Mint out, then how to install it on your machine. This is an image of the Mint operating system which you can use to run or install the operating system. No harm, no foul. So let’s get started.

SecureWorld News
FEBRUARY 15, 2023
Vulnerability management comprises the entirety of workflows geared toward maintaining an up-to-date inventory of a company's digital assets, checking them for imperfections, and addressing the detected security loopholes. The latter aims to enhance corporate security, in general, and incident response, in particular.
Kitaboo
NOVEMBER 28, 2019
Compatibility with Multiple Devices, Operating Systems and Browsers. Since there are different operating systems available and also web browsers that are either specific to each OS or accessible across all systems, the content you publish must be accessible on most if not all operating systems and browsers.

CIO Business Intelligence
NOVEMBER 29, 2023
Don’t sign with a provider unless you have an agreement so you know how to get your data out and how to replicate those software services elsewhere,” he says. Security is a good example. “If If your security needs are high, generic cyber security might not be sufficient,” says Holcombe.

CIO Business Intelligence
NOVEMBER 28, 2022
Here’s our view on how to make the Free Dimension work for you: 1. Sembcorp Industries , one of Singapore’s largest energy players, for example, has adopted Microsoft Cloud to help its employees improve productivity and well-being, as they work to build an energy operating system at scale for a green, sustainable future.

CIO Business Intelligence
MAY 31, 2022
Their accounts face greater risk since your organization has little control over their devices, operating systems, browsers, and apps. It adds complexity and cost to your security stack and frustrates customers. Likewise, a Transmit Security survey found that 92% would rather leave a site than recover or reset their credentials.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content