International Malware Takedown Seized 100+ Servers
Tech Republic Security
MAY 31, 2024
‘Operation Endgame’ is an ongoing, law enforcement effort to disrupt botnets, malware droppers and malware-as-a-service.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Tech Republic Security
MAY 31, 2024
‘Operation Endgame’ is an ongoing, law enforcement effort to disrupt botnets, malware droppers and malware-as-a-service.
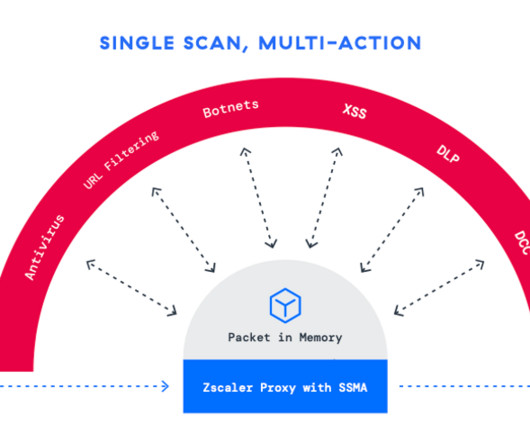
Network World
DECEMBER 20, 2024
Attackers are using encrypted channels to bypass traditional defenses, concealing malware, phishing campaigns, cryptomining/cryptojacking, and data theft within encrypted traffic. Malware dominates the landscape: Malware remains the most prevalent encrypted threat, representing 86.5% Encrypted threats accounted for 87.2%
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Tech Republic Security
MARCH 14, 2024
To protect company data and reputation, it is essential to ensure that the network is secured from unauthorized access, data loss, malware infestations and security breaches. This can include internal and external systems, either company-owned or leased/rented/subscribed to. This must be done.

SecureWorld News
MARCH 13, 2025
A recent report from Tenable highlights how DeepSeek R1, an open-source AI model, can generate rudimentary malware, including keyloggers and ransomware. While the AI-generated malware required manual debugging to function properly, its mere existence signals an urgent need for security teams to adapt their defenses.

CIO Business Intelligence
MARCH 4, 2025
The report also highlighted that Chinese groups continue to share malware tools a long-standing hallmark of Chinese cyber espionage with the KEYPLUG backdoor serving as a prime example. Vault Panda has used many malware families shared by Chinese threat actors, including KEYPLUG, Winnti, Melofee, HelloBot, and ShadowPad.

Tech Republic Security
MAY 19, 2024
By establishing an antivirus policy, organizations can quickly identify and address malware and virus threats, as well as detect and appropriately respond to incidents. The purpose of this Antivirus Policy, written by Madeline Clarke for TechRepublic Premium, is to provide guidelines for.

CTOvision
JULY 29, 2014
Three Questions on Automated Malware Removal with Bob Gourley, Cognitio Corp and CTOVision. While there’s still an emphasis – and related spending – on malware detection, most incident response teams are actually overwhelmed by vast number of security alerts they receive. Another day, another data breach. Bob Gourley: That’s simple.

CTOvision
OCTOBER 29, 2014
This quote summarizes the importance of online encryption policy and hands-on implementation within an organization. Through an online encryption policy, you can mitigate the risks and avoid these cases, whether you’re a profit or a non-profit organization. What is an online encryption policy? Corporate B2B and B2C companies.

CIO Business Intelligence
DECEMBER 3, 2024
More than ever, businesses are concerned that threat actors could place malware on their OT networks and syphon valuable data over an extended period. Andre Ferreira, Director of Enterprise 5G Customer Solutions at NTT DATA, explains: “Increasing IT-OT convergence exposes OT networks to a broader range of external threats.

Network World
MARCH 23, 2022
As knowledge workers became increasingly mobile, and as BYOD initiatives spread across organizations, NAC solutions evolved to not only authenticate users, but also to manage endpoints and enforce policies. NAC solutions will, for instance, make sure that the endpoint has up-to-date antivirus and anti-malware protections.

CIO Business Intelligence
MARCH 4, 2025
The report also highlighted that Chinese groups continue to share malware tools a long-standing hallmark of Chinese cyber espionage with the KEYPLUG backdoor serving as a prime example. Vault Panda has used many malware families shared by Chinese threat actors, including KEYPLUG, Winnti, Melofee, HelloBot, and ShadowPad.

CIO Business Intelligence
MARCH 14, 2025
In the past few months, infostealer malware has gained ground. Both the software and its data are sold on the dark web in the form of Malware-as-a-Service (MaaS). Both the software and its data are sold on the dark web in the form of Malware-as-a-Service (MaaS).
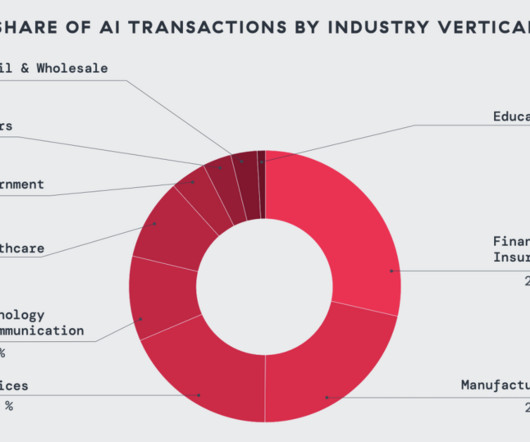
CIO Business Intelligence
MARCH 25, 2025
As organizations work to establish AI governance frameworks, many are taking a cautious approach, restricting access to certain AI applications as they refine policies around data protection. AI-powered cyberthreat protection: Detect and block AI-generated phishing campaigns, adversarial exploits, and AI-driven malware in real time.

Network World
FEBRUARY 6, 2025
Three new boxes in the FortiGate G Series portfolio the 70G, 50G, and 30G include integrated firewall, intrusion prevention, malware and ransomware protection, SD-WAN, and switching capabilities, all of which can be managed via the vendors FortiManager centralized management platform.

Network World
MAY 9, 2019
Cisco has added support for Advanced Malware Protection (AMP) to its million-plus ISR/ASR edge routers, in an effort to reinforce branch and core network malware protection at across the SD-WAN. Cisco last year added its Viptela SD-WAN technology to the IOS XE version 16.9.1 To read this article in full, please click here

CTOvision
MAY 22, 2014
Organizations are giving more priority to development of information security policies, as protecting their assets is one of the prominent things that needs to be considered. Lack of clarity in InfoSec policies can lead to catastrophic damages which cannot be recovered. Security policies are tailored to the specific mission goals.

Network World
APRIL 9, 2025
Support for automating network configuration and security policy updates, validation and correction of existing configurations. The package employs AI and machine learning techniques to large-scale data analysis with the goal of helping detect and neutralize emerging malware threats.

Network World
OCTOBER 21, 2024
Access is authorized based on business policies informed by identity and context. Cybercriminals began to use social engineering techniques to trick people into giving up their personal information, and they developed new malware that could evade traditional security measures.

Network World
OCTOBER 18, 2024
Overall, ThreatLabz tracked a rise in financially motivated mobile attacks – with 111% growth in spyware and 29% growth in banking malware – most of which can bypass multifactor authentication (MFA). Top Mobile and IoT/OT trends Rise in financially-motivated mobile threats, including a 111% rise in spyware and 29% growth in banking malware.

Network World
AUGUST 27, 2024
Target customers are enterprises and telecom service providers looking to defend against malware and ransomware attacks, and to defend against nation-state actors. VMware’s vDefend platform protects east-west traffic with zero trust, microsegmentation, zone-level segmentation, and malware and ransomware defense.

Network World
FEBRUARY 20, 2025
All components, including advanced security features like sandboxing and malware detonation that traditionally required cloud services, can run within the customers environment. Organizations can integrate their own threat intelligence and customize security policies while maintaining complete data sovereignty.

Network World
SEPTEMBER 12, 2024
NIST, other government agencies, and industry bodies point towards the policy enforcement point (PEP) as the gateway device or service that performs this separation, gating access based on different authentication and authorization requirements, depending on the sensitivity of the resource.

CIO Business Intelligence
NOVEMBER 14, 2023
Unsanctioned devices often lack essential security controls and don’t adhere to corporate security policies. Malware is the top threat to IoT/OT With so many vulnerabilities plaguing IoT devices, these devices are attractive and relatively easy entry points into corporate networks for attackers.

CTOvision
MAY 2, 2014
When malware makes is into the enterprise, through gateways, guards or via tricky deception of your workforce, the code seeks to remain low-key. By pulling together all relevant data and knowing what is out of place, Hexis has been able to design in an advanced, policy drive means to engage malicious code at machine speeds.

Network World
MAY 30, 2024
Businesses can extend secure connected experiences everywhere using Cisco Talos-powered cybersecurity capabilities—firewall policies, content filtering, intrusion detection and prevention (IDS and IPS), advanced malware protection (AMP), and more—using both wired WAN and FWA.”

CIO Business Intelligence
OCTOBER 25, 2023
Companies must be acutely aware of ensuring employee compliance with both AI utilization and general security policies to ensure that private data or sensitive information is not inadvertently shared or leaked. Businesses must remind employees that these are not private or confidential when using chat AI tools.

Network World
APRIL 10, 2025
Secure branch offices and enable rapid response to security incidents and consistent security policy enforcement across all sites. The visibility reduces the risk of malware, data breaches, and cyberattacks for Google Cloud customers. Gain access to Googles global network.

Network World
JUNE 13, 2024
The life cycle of a cyberattack Regardless of the method that threat actors use to commit cyberattacks—phishing, malware, and, yes, ransomware—the stages of every attack are remarkably similar. In cyber terms, this translates into the user, device, or vulnerable asset being compromised by a phishing or malware attack.

TechSpot
JANUARY 29, 2023
The researchers identified the SwiftSlicer malware deployed during a cyberattack targeting Ukrainian technology outlets. The malware ware was written using a cross-platform language called Golang, better known as Go, and uses an Active Directory (AD) Group Policy attack vector.

Network World
MAY 19, 2016
The Cisco Web Security Appliance (WSA) is a line of security devices that inspect Web traffic going in and out of an organization in order to detect malware, prevent data leaks, and enforce Internet access policies for users and applications. The devices run an operating system called Cisco AsyncOS.

CIO Business Intelligence
JULY 25, 2024
Malware, phishing, and ransomware are fast-growing threats given new potency and effectiveness with AI – for example, improving phishing attacks, creating convincing fake identities or impersonating real ones.

CIO Business Intelligence
FEBRUARY 10, 2025
It enables attackers to automate phishing campaigns, create evasive malware, expedite threat development through AI, and offer Ransomware-as-a-Service (RaaS). Cant inspect encrypted traffic and enforce real-time security policies at scale. This progress, while groundbreaking, also presents new challenges.

Dataconomy
MARCH 21, 2025
Malware has become an omnipresent threat in todays digital landscape, affecting devices, networks, and even entire organizations. Understanding the nature of malware can equip individuals and enterprises with the knowledge needed to defend against its potentially devastating effects. What is malware?

CTOvision
NOVEMBER 26, 2013
Solution provides real-time detection, identification, and mitigation of advanced malware that operates in endpoint volatile memory . product suite, combines Triumfant’s unique, patented malware detection software with new tools that can accurately track malware functionality operating in the volatile memory of the endpoint machine.

Network World
MAY 4, 2017
When Microsoft made it possible for enterprises to quickly resolve incompatibilities between their applications and new Windows versions, it didn't intend to help malware authors as well. Yet, this feature is now abused by cybercriminals for stealthy and persistent malware infections.

CIO Business Intelligence
JULY 14, 2022
And they follow the same corporate policies from managed and unmanaged devices and across every component – from the secure web gateway (SWG) to the cloud access security broker (CASB) to zero trust private access, and even on-premises devices. Use case 3: proprietary applications in the public cloud.

Network World
MARCH 20, 2017
These successful social engineering methods often use phishing and malware. But deceptive information assailants have more tools and approaches to draw on than these.

Network World
JUNE 6, 2024
Gartner cautions that Cloudflare lacks some features, such as file malware sandboxing, DEM, and full-featured built-in reporting and analytics. Features include the ability to support remote browser isolation, DLP, and cloud malware detection. How easy is it to apply security policies? Will I have fewer consoles?

CIO Business Intelligence
FEBRUARY 16, 2024
Copilot is integrated into Microsoft 365 and automatically inherits the company’s security, compliance, and privacy policies and processes. Copilot combines large language models (LLMs) with the bank’s data, providing staff access to a virtual PA, copywriter and analyst.

CIO Business Intelligence
JUNE 13, 2024
As our warfighters, who are closest to the problems, are learning the technology, we are leveraging their insights to inform future policy, acquisition and investment decisions.” Users will have the opportunity to provide feedback to shape policies and inform procurement conversations with vendors of such tools in future.

Network World
DECEMBER 10, 2024
Cato IoT/OT Security offers network and security teams device discovery and classification features, as well as policy enforcement and threat detection capabilities in its Cato SASE Cloud Platform. These capabilities will not only better secure these devices, but they will also simplify the management of IoT/OT devices, Cato says.

SecureWorld News
FEBRUARY 26, 2025
Dubai-based exchange Bybit was targeted in a malware-driven attack that resulted in the theft of approximately $1.46 The Bybit theft resulted from malware-driven manipulation of cold wallet transactions, exploiting multi-signature vulnerabilities," Soroko said. billion in crypto assets.

CIO Business Intelligence
JUNE 25, 2024
Malicious browser extensions can introduce malware, exfiltrate data, or provide a backdoor for further attacks. Advanced threat intelligence and machine learning algorithms detect anomalies, phishing attempts, malicious file upload and download, and malware infections. To learn more, visit us here.

CTOvision
SEPTEMBER 5, 2013
. “I think that’s a certainty,” said Jim Lewis, a senior fellow with the Center for Strategic and International Studies and the director of the Technology and Public Policy Program.’ Via The Hill, more here. ” Via FedScoop, more here. ” Via ComputerWorld, more here. ” Via InfoSecurity, more here.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content