Electronic data disposal policy
Tech Republic Security
MARCH 15, 2023
The post Electronic data disposal policy appeared first on TechRepublic. The post Electronic data disposal policy appeared first on TechRepublic.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Tech Republic Security
MARCH 15, 2023
The post Electronic data disposal policy appeared first on TechRepublic. The post Electronic data disposal policy appeared first on TechRepublic.

Tech Republic Security
MARCH 4, 2022
The cloud is becoming the norm when it comes to data storage, but it's not without its challenges. The right policies and procedures can go a long way toward safely storing data in the cloud. The post Go-to resources for safe, secure cloud storage appeared first on TechRepublic.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Network World
MARCH 2, 2023
IBM and data security and backup provider Cohesity have formed a new partnership, calling for Cohesity’s data protection functionality to be incorporated into an upcoming IBM storage product suite, dubbed Storage Defender, for better protection of end-user organizations’ critical information.

CIO Business Intelligence
DECEMBER 20, 2024
Its an offshoot of enterprise architecture that comprises the models, policies, rules, and standards that govern the collection, storage, arrangement, integration, and use of data in organizations. It includes data collection, refinement, storage, analysis, and delivery. Cloud storage. Ensure security and access controls.

Tech Republic Security
JULY 30, 2023
The Data Encryption Policy’s purpose is to define for employees, computer users and IT department staff the encryption requirements to be used on all computer, device, desktop, laptop, server, network storage and storage area network disks, and drives that access or store organization information to prevent unauthorized access to organization communications, (..)

CIO Business Intelligence
AUGUST 26, 2024
Fractured policy frameworks compromise security and compliance initiatives, increase risk, and decrease service levels. Adopting the same software-defined storage across multiple locations creates a universal storage layer. Adopting the same software-defined storage across multiple locations creates a universal storage layer.

Network World
MARCH 18, 2025
The companies rolled out the Cisco Secure AI Factory with Nvidia, which brings together Cisco security and networking technology, Nvidia DPUs, and storage options from Pure Storage, Hitachi, Vantara, NetApp, and VAST Data. Hypershield uses AI to dynamically refine security policies based on application identity and behavior.

Tech Republic Security
MARCH 30, 2023
PURPOSE This Media disposal policy from TechRepublic Premium provides specific instructions for ensuring organization data is properly protected when disposing of old storage media.

CIO Business Intelligence
NOVEMBER 19, 2024
The data is spread out across your different storage systems, and you don’t know what is where. Maximizing GPU use is critical for cost-effective AI operations, and the ability to achieve it requires improved storage throughput for both read and write operations. Planned innovations: Disaggregated storage architecture.

Network World
FEBRUARY 19, 2025
Seagates standard policy grants a five-year warranty on retail versions of IronWolf Pro drives. We have no evidence right now, but I believe there must be cases because Seagate is not alone in the storage world, Luis Labs, who authored the investigation report, told Network World.

CTOvision
OCTOBER 29, 2014
This quote summarizes the importance of online encryption policy and hands-on implementation within an organization. Through an online encryption policy, you can mitigate the risks and avoid these cases, whether you’re a profit or a non-profit organization. What is an online encryption policy? Corporate B2B and B2C companies.

Tech Republic Security
APRIL 17, 2024
The Data Encryption Policy’s purpose is to define for employees, computer users and IT department staff the encryption requirements to be used on all computer, device, desktop, laptop, server, network storage and storage area network disks, and drives that access or store organization information to prevent unauthorized access to organization communications, (..)

Computer Weekly
JUNE 26, 2017
News publishing corporation saves up to 40% on hardware and software costs by switching in-house hardware for a cloud-first policy, using Zadara cloud storage as a backup target

Network World
FEBRUARY 10, 2025
Unlike traditional cryptocurrency mining that relies on GPUs, Chia mining is storage-intensive, leading to a surge in HDD demand during its peak. Organizations should establish strict procurement policies to mitigate the risks posed by counterfeit hardware in their IT infrastructure.

CIO Business Intelligence
JANUARY 7, 2025
Its a good idea to establish a governance policy supporting the framework. Creating awareness of the policy of least privilege and addressing frustrations when cloud users ask for more to play with, and as a cloud CoE team, you are rightfully holding your ground that comes with it.

CIO Business Intelligence
OCTOBER 30, 2024
This requires greater flexibility in systems to better manage data storage and ensure quality is maintained as data is fed into new AI models. They may implement AI, but the data architecture they currently have is not equipped, or able, to scale with the huge volumes of data that power AI and analytics.
Network World
SEPTEMBER 25, 2024
NetApp’s BlueXP offers a single integrated pane of glass for monitoring, troubleshooting and managing NetApp storage systems including OnCommand Network Attached Storage Protocol (ONTAP), All flash (AFF), and the Microsoft-NetApp developed Azure NetApp Files (ANF). “By

CIO Business Intelligence
MARCH 25, 2025
As a result, organizations are investing in AI infrastructure, including accelerated compute, reliable networking, and sufficient storage, to support their initiatives. Despite this need, 76% of respondents admitted their organizations lack comprehensive AI policies.

Network World
MARCH 17, 2025
As such they benefit from pod networking and storage, managed through standard Kubernetes tools like kubectl. KubeVirt takes advantage of Kubernetes-native security, ensuring that policies are applied consistently across all environments, including virtual machines. What can you do with KubeVirt? Built-in security.

CIO Business Intelligence
APRIL 26, 2022
Modernizing primary storage is key to transformation. In powering a transformation journey with an edge-to-cloud, cloud operational model, finding the right solution for primary storage is critical. What’s needed is STaaS — for all. That’s what will unlock the benefits of the cloud operational model on-prem.

Network World
OCTOBER 3, 2024
Hyperconverged infrastructure (HCI) Hyperconverged infrastructure combines compute, storage and networking in a single system and is used frequently in data centers. Infrastructure as a service (IaaS): IaaS provides the building blocks of cloud computing — servers, storage and networking.

Tech Republic Cloud
FEBRUARY 12, 2023
The OneDrive Cloud Usage Policy defines the practices and behaviors organization representatives must follow when using any Microsoft OneDrive cloud file storage account to execute organization services, process organization data, or access or store organization information.

Network World
JUNE 12, 2024
On my podcast, The Backup Wrap-up , we recently reviewed 10 cloud catastrophes that occurred over the last 15 years (listed alphabetically): Carbonite (2009): Due to lack of redundancy and the use of consumer-grade storage arrays, Carbonite lost the backup data of thousands of customers in a major data loss incident.

CIO Business Intelligence
OCTOBER 22, 2024
Microgrids are power networks that connect generation, storage and loads in an independent energy system that can operate on its own or with the main grid to meet the energy needs of a specific area or facility,” Gartner stated.

Network World
MAY 16, 2024
That package combines Cisco’s SaaS-managed compute and networking gear with Nutanix’s Cloud Platform, which includes Nutanix Cloud Infrastructure, Nutanix Cloud Manager, Nutanix Unified Storage, and Nutanix Desktop Services. Data Center, Enterprise Storage, Network Management Software, Servers

Tech Republic Cloud
JANUARY 22, 2023
Third-party cloud-based file storage applications such as Dropbox, OneDrive and Google Drive have all contributed to the success of business cloud data storage. Cloud data storage offers many benefits to consumers and companies. Cloud data storage offers many benefits to consumers and companies.

Anoop
JUNE 23, 2021
The post How to Configure Storage Sense in Intune | Endpoint Manager appeared first on HTMD Blog #1 by Jitesh Kumar. Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link]. and Facebook Page to get the latest updates.

CIO Business Intelligence
MARCH 13, 2025
VCF brings together compute, storage, networking, and automation resources in a single platform that can host VMs and containerized applications. In this way, VCF simplifies management, operations, policies, and security across the entire application portfolio. VMware Cloud Foundation (VCF) is one such solution.
Network World
FEBRUARY 13, 2025
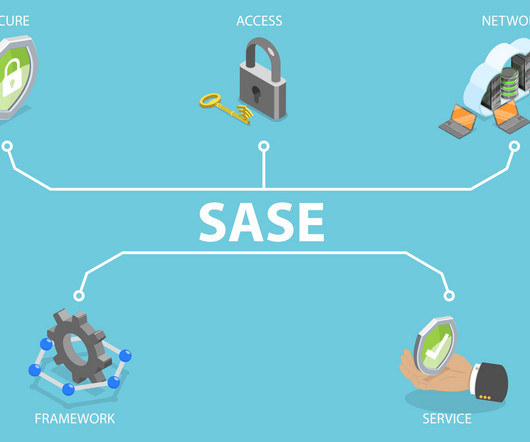
Secure Access Service Edge (SASE) is a network architecture that combines software-defined wide area networking (SD-WAN ) and security functionality into a unified cloud service that promises simplified WAN deployments, improved efficiency and security, and application-specific bandwidth policies. What is SASE?
The Verge
NOVEMBER 11, 2020
After five years of offering unlimited free photo backups at “high quality,” Google Photos will start charging for storage once more than 15 gigs on the account have been used. Google is also introducing a new policy of deleting data from inactive accounts that haven’t been logged in to for at least two years. Why the change?

CIO Business Intelligence
FEBRUARY 18, 2025
Enterprises often purchase cloud resources such as compute instances, storage, or database capacity that arent fully used and, therefore, pay for more service than they actually need, leading to underutilization, he says. Essentially, cloud cost management is a shared responsibility between the enterprise and vendor, Kulkarni says.

CIO Business Intelligence
DECEMBER 20, 2022
Overly permissive access privileges Overly permissive access policies and privileges enable expanded access to far more assets than needed. Storage misconfiguration Misconfiguration opportunities abound when it comes to cloud storage. You may think user credentials are limited only to find out later that they were unlimited.

Network World
SEPTEMBER 30, 2024
In the complaint, the group, which called itself the Coalition for a Level Playing Field , accused Microsoft of pushing OneDrive “wherever users deal with file storage and Teams is a default part of Windows 11. This makes it nearly impossible to compete with their SaaS services.

CIO Business Intelligence
SEPTEMBER 6, 2024
Enterprises and their IT teams need data – structured or unstructured – to have a consistent manager view, be discoverable to employees across departments, be secure and follow governance policies, and be cost-effective regardless of whether data is in the cloud or on-premises. This approach is risky and costly.
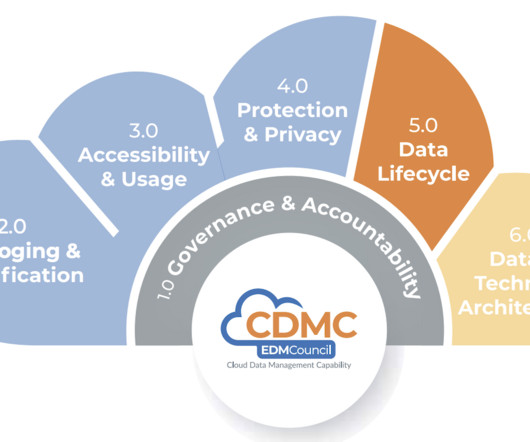
Tech Republic Security
JULY 7, 2023
The Council’s first benchmark found that 84% of companies have not implemented ethical access, use and outcome policies and procedures per their cloud agendas. The post EDM Council Survey: Management of Cloud Data Deployment is Lacking appeared first on TechRepublic.

CIO Business Intelligence
MARCH 19, 2025
For instance, cloud storage strategies can be adjusted to prefer providers with carbon-neutral commitments, and AI model training can be optimized to reduce computational costs. For example, reducing redundant data storage or optimizing cloud resource usage can lead to financial and environmental benefits.

CIO Business Intelligence
JUNE 3, 2024
For generative AI, a stubborn fact is that it consumes very large quantities of compute cycles, data storage, network bandwidth, electrical power, and air conditioning. In storage, the curve is similar, with growth from 5.7% of AI storage in 2022 to 30.5% Facts, it has been said, are stubborn things.

The Verge
NOVEMBER 12, 2020
Back in 2019, photo storage service Flickr changed its previous policy of offering 1TB of free storage to its users, limiting free storage to 1,000 photos instead. Once you hit that 15GB wall, you will have to buy into the Google One service to increase your storage capacity. Photo by Vlad Savov / The Verge.

CIO Business Intelligence
OCTOBER 15, 2024
The new Global Digitalization Index or GDI jointly created with IDC measures the maturity of a country’s ICT industry by factoring in multiple indicators for digital infrastructure, including computing, storage, cloud, and green energy. This research found that a one-US-dollar investment in digital transformation results in an 8.3-US-dollar

CIO Business Intelligence
FEBRUARY 10, 2025
Zero trust prevents compromise through context-aware policies and, unlike hardware and virtual appliances, a high-performance cloud with the scalability necessary to inspect encrypted traffic (where most threats hide (but more on that below (arent parentheses fun?))).

CIO Business Intelligence
JULY 28, 2023
Data lifecycle management is essential to ensure it is managed effectively from creation, storage, use, sharing, and archive to the end of life when it is deleted. Data lifecycle management covers the processes, policies, and procedures to ensure data is effectively managed through its lifecycle.

Network World
JULY 17, 2024
Companies can use Apstra’s automation capabilities to deliver consistent network and security policies for workloads across physical and virtual infrastructures. Apstra works by keeping a real-time repository of configuration, telemetry and validation information to ensure a network is doing what the organization wants it to do. headquarters.

CIO Business Intelligence
MARCH 31, 2025
Optimized hardware Broadcoms role in delivering specialized accelerated networking and storage, combined with performance-optimized and production-supported NVIDIA GPUs, ensure that sovereign AI systems can be powered by cutting-edge hardware capable of processing large datasets and complex AI models without relying on foreign providers.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content